Securing Non-Human Identities. Everywhere.
Secure API Keys, Secrets, Tokens, Service Accounts, and AI Agents Across Cloud, SaaS, and On-Premise environments
Trusted by world-recognized brands
Extending Zero Trust to NHIs











Visibility
Discovery and Inventory
Identify, catalog, and manage NHIs with full oversight. Achieve unified visibility across all environments
Automation
Real-Time Monitoring
Continuously analyze NHI usage in real-time. Establish a trust baseline based on organizational context
Access Control
Enforcement
Constrain NHIs to approved scopes and operational boundaries. Enforce fine grained, Least Privilege policies
The Non-Human Identity Landscape is
Hyper Fragmented
Across Cloud, SaaS, On-Prem environments, code repositories, CI/CD, Data Warehouses, and more
Massively Scaled
Outpacing human identities 82:1, with AI-driven workloads compounding the growth curve
Privileged by Design
Holds critical privileges and extensive access, essential for mission critical automated processes
Lacking Controls
Lacks inherent security controls such as MFA and conditional access policies
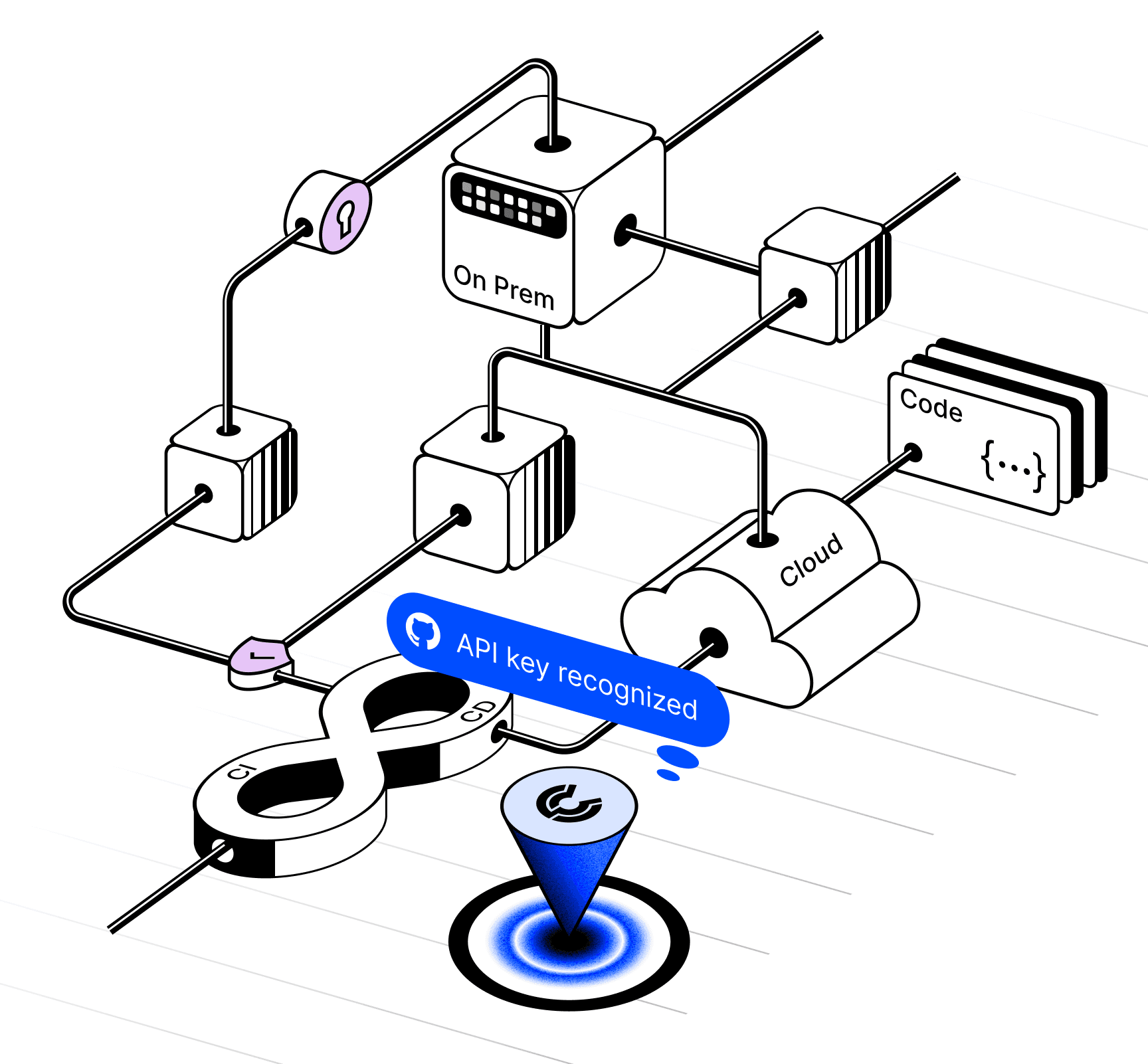
Industry-First Universal Non-Human Identity Security Platform
Get the Full Picture
Automatically and continuously discover and correlate all NHIs across the entire ecosystem with a contextualized inventory, including API keys, tokens, secrets, service accounts, and certificates.
Learn more ->The Clutch Approach
Seamlessly manage and secure Non-Human Identities with Clutch's Workflows engine
Clutch's Workflows automate security tasks, ensuring swift responses to NHIs. Custom triggers handle scenarios like secret expirations, NHI detection, and employee offboarding, boosting efficiency.
Understanding the full context of any Non-Human Identity with Clutch’s Identity Lineage™
Clutch's Non-Human Identity Lineage™ enables you to comprehend the full extent of usage, interactions, and access of all your NHIs - intuitively, simply, and with ease - through simple visualization.
Proactively shield your organization with Zero Trust Protection
Zero Trust protection engine enables you to fortify your defenses by proactively applying best practice policies, all without the need for endless rotations and being dependent on IT and Engineering teams.
Instant Setup, Immediate Impact
Jenkins
PagerDuty
Kubernetes
Amazon EC2
SAP
Okta
CircleCI
GitHub
HashiCorp
Delinea
LastPass
Microsoft
Salesforce
PostgreSQL
Azure AD
CrowdStrike
1Password
Splunk
Oracle
Slack
Datadog
Terraform
Azure
CyberArk
Amazon EKS
Workday
Google Cloud
Snowflake
Databricks
Bitbucket
GitLab
AWS
One-Click Deployment
Connect to all your terrains and environments: integrate any CSP, app, and pipeline with a single click and zero friction. No agents required.
Zero-Time to Value
Immediate Time-to-Value onboarding and mapping of all your NHIs and their associated risks. Get actionable insights and recommendations at your fingertips in minutes.
Your NHI Realm Secured
Our Zero Knowledge Architecture keeps your data within your network, while robust processes and recommendations ensure agility and peak performance.
In today's threat landscape, having a holistic NHI security solution is essential. Clutch's platform offers a holistic coverage across all organizational environments and landscapes. The integrated context it provides allows teams, to fully understand the extent of NHIs across the organization and take a risk based context approach to manage NHIs, while minimizing friction between teams.