Zero Trust Enforcement
Clutch enforces Zero Trust for NHIs with continuous verification, least privilege access, and ephemeral identities for enhanced security.
The Challenge
In the cybersecurity industry, the adoption of Zero Trust for human users has become a standard practice, but the question of trust is even more critical when it comes to Non-Human Identities.
Ensuring a comprehensive Zero Trust architecture for NHIs is essential to continuously verify and validate the use of every identity, preventing unauthorized access and maintaining a robust security posture across all digital environments, all without disrupting business operations or involving other teams.
The Clutch Solution
Proactively Shield Your Organization with Zero Friction
Zero Trust
Continuously certify and verify consumers of all NHIs
Ephemeral Identities
Embrace secretless access over static, long-lived credentials
Flexible Approach
Adapt to organization’s unique risk appetite
Context-driven
Context-aware security through leveraging organizational data sources
Clutch’s industry-only Zero Trust-driven platform enables organizations to proactively minimize the attack surface and prevent risks before they arise.
By analyzing and learning behavior and access patterns over time, Clutch identifies potential risks associated with each NHI and offers proactive strategies to monitor and enforce least privilege access policies, resulting in robust security posture:
Clutch empowers security teams to extend the same Zero Trust approach used for their human identities to Non-Human ones, by continuously monitoring and validating NHI usage to prevent unauthorized access.
Even if an NHI is compromised, it remains unusable by attackers due to Clutch's ongoing verification processes.
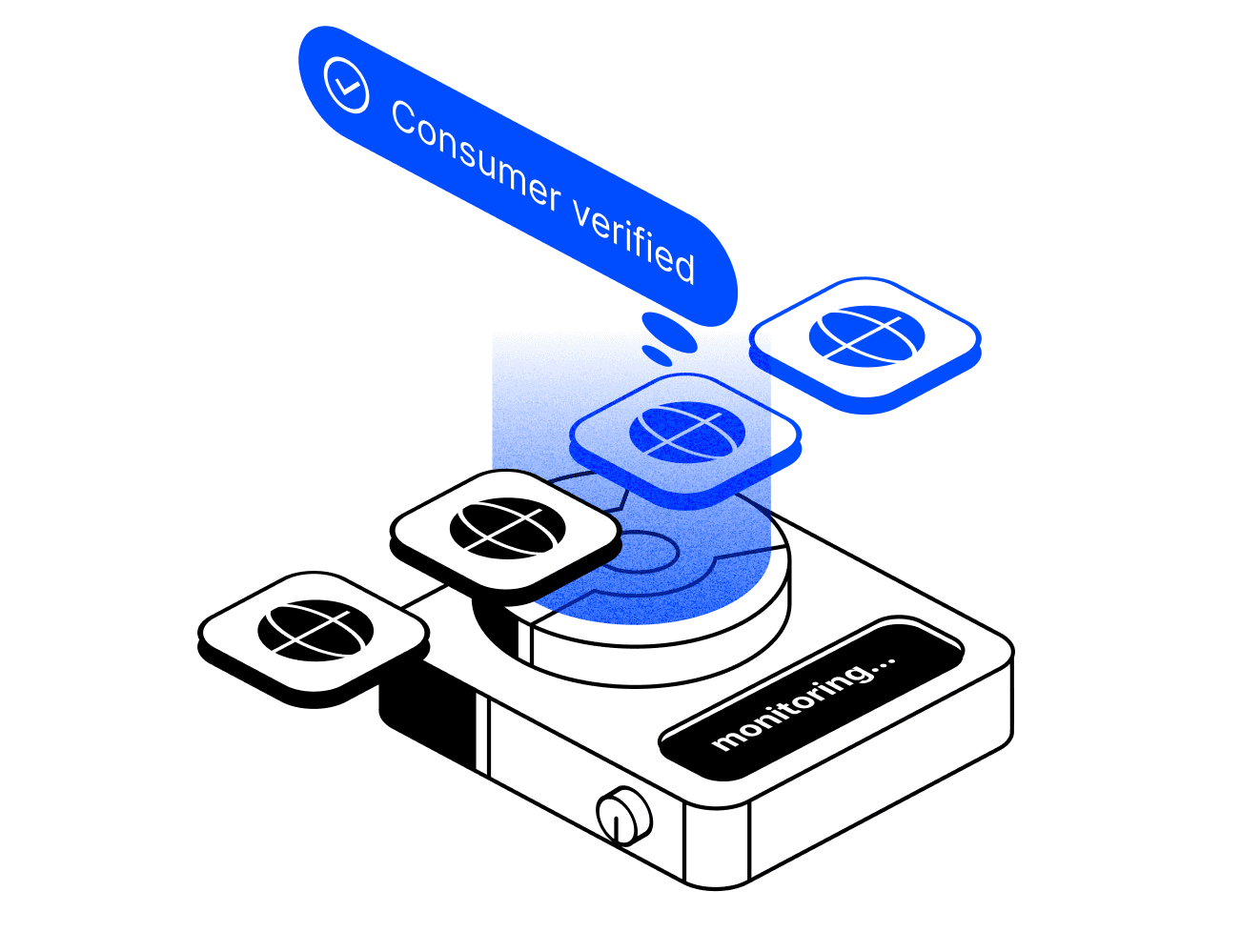
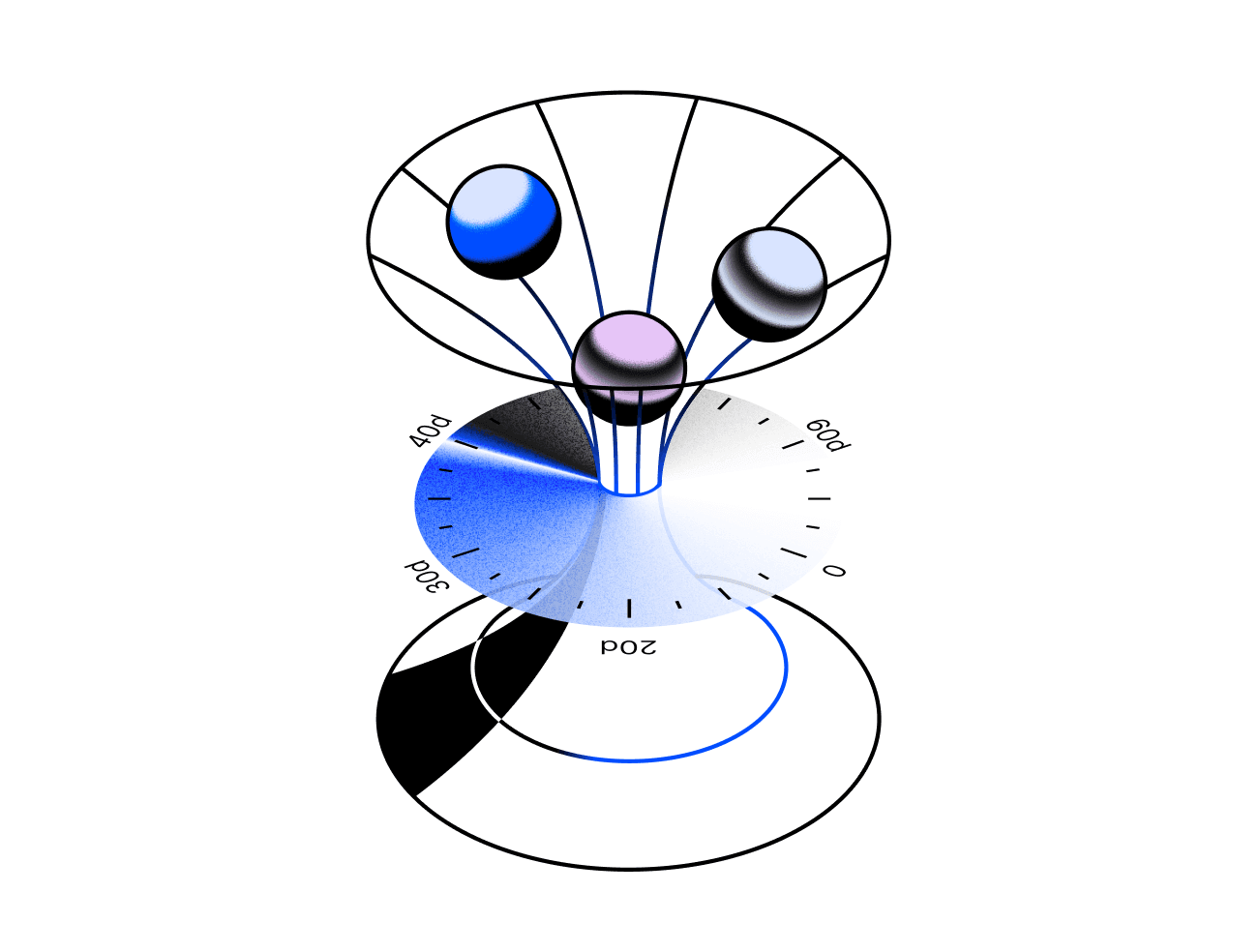
Clutch facilitates the transition from static, long-lived NHIs to ephemeral, auto-expiring identities.
This shift dramatically reduces exposure windows, limiting risk in the event of a compromise.