Universal Non-Human Identity Security Platform
Visibility, Control, and Security for Every NHI
Securing the Backbone of Modern Enterprise with a Single Platform
Automatically discover and correlate all NHIs with a contextualized inventory
Effortlessly manage the NHI lifecycle and address governance gaps
Optimize posture and drastically reduce the attack surface by mitigating NHI-based risks
Immediately detect suspicious NHI behavior and respond to breaches to minimize impact
Proactively apply a Zero Trust approach without affecting business continuity
Secure all Non-Human Identities. Everywhere.
How Clutch Works
Seamlessly Fetches Data from the Entire Ecosystem
Clutch collects information from multiple sources of truth across the entire ecosystem: Cloud, SaaS, on-prem, Code and CI/CD, Vaults, RPA, Data Warehouses, and more. Clutch's complete coverage allows to not only discover and map all NHIs in the ecosystem, but also to correlate their use across disparate technologies, providing deep insight into the environment
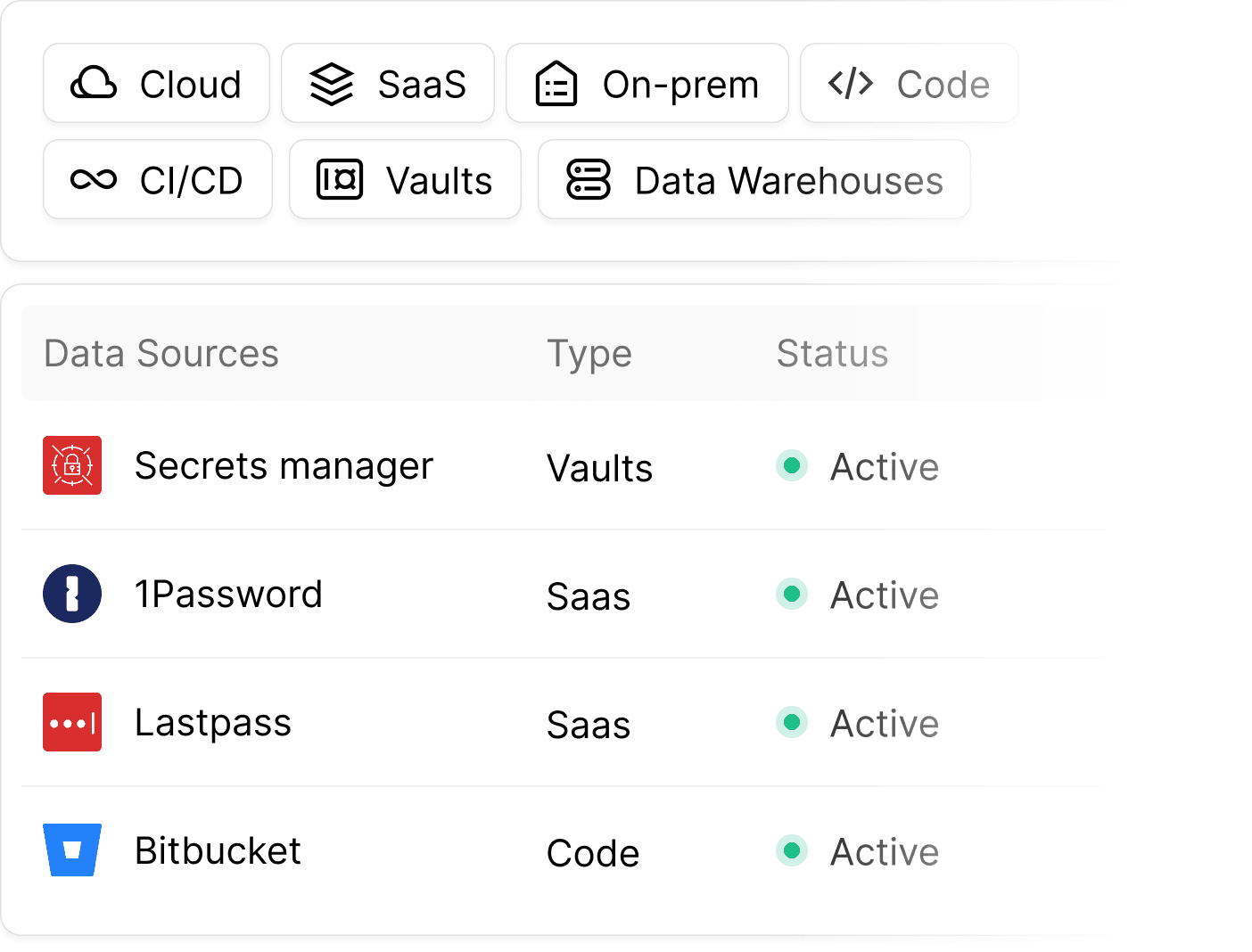
Intuitively Visualizes and Contextualizes All Non-Human Identities
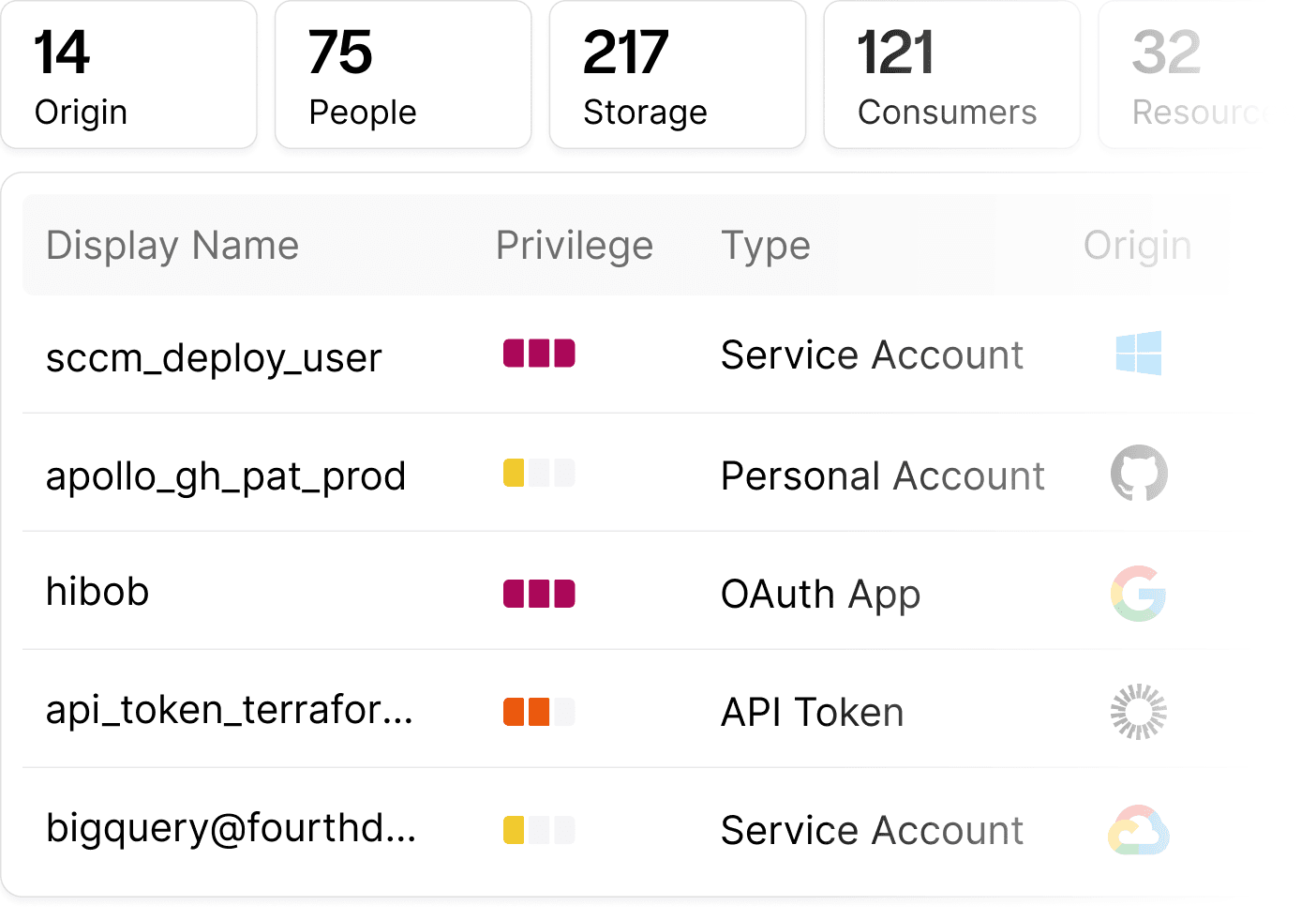
Clutch intuitively visualizes relationships and interactions between NHIs and associated elements by fusing, analyzing, and correlating multi-terrain data. This process reveals comprehensive insights into NHI usage and access, including origin, related people, storage, consumers, and resources within the organization.
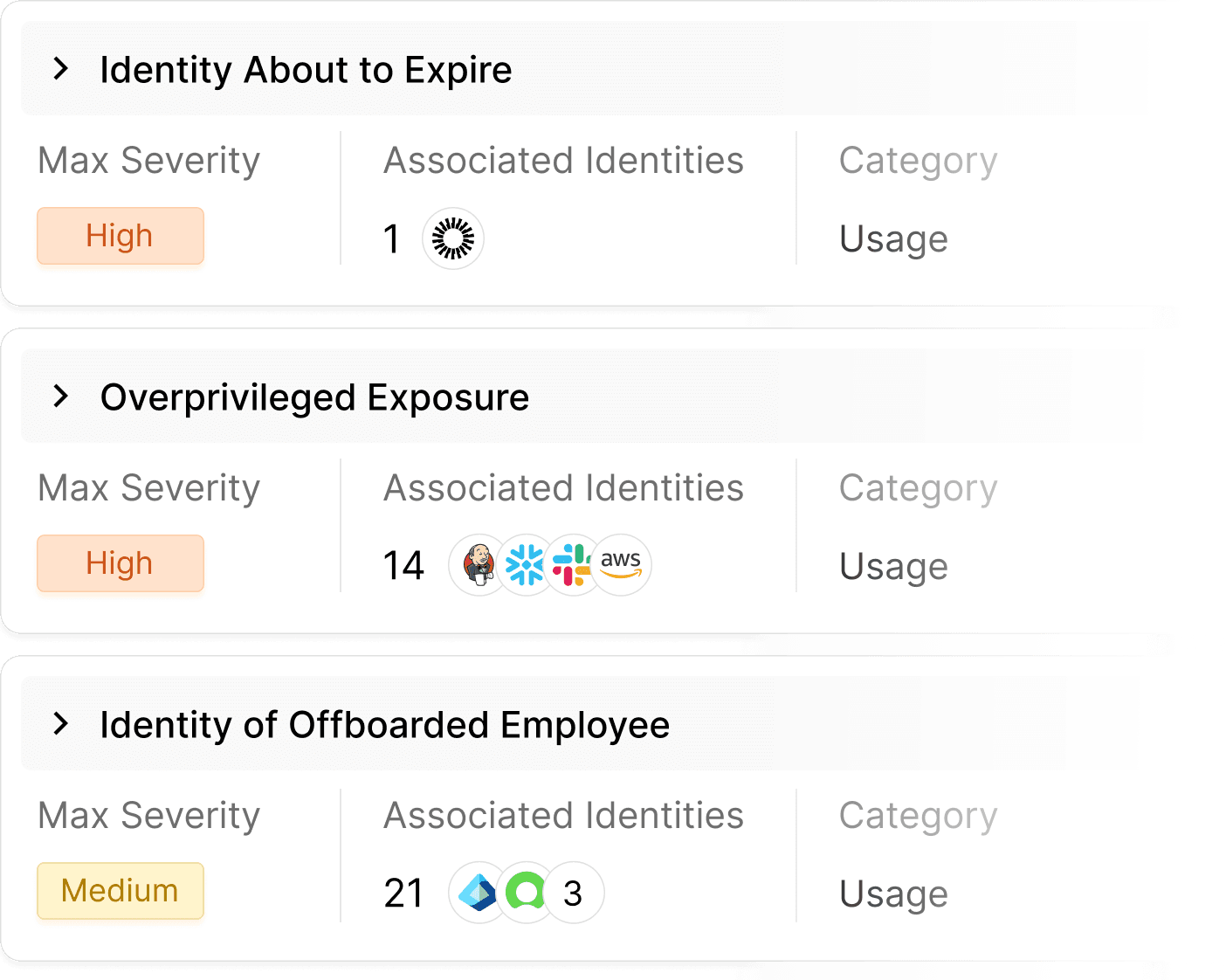
Efficiently Identifies Risks and Opportunities and Empowers Remediation
Clutch discovers and prioritizes risks based on identity context and lifecycle, offering out-of-the-box remediation plans to accelerate security posture and ensure full protection. Insights and recommendations span from lifecycle management actions to reactive risk management and proactive Zero Trust protection mechanisms, effectively addressing potential threats based on the organization's risk appetite.
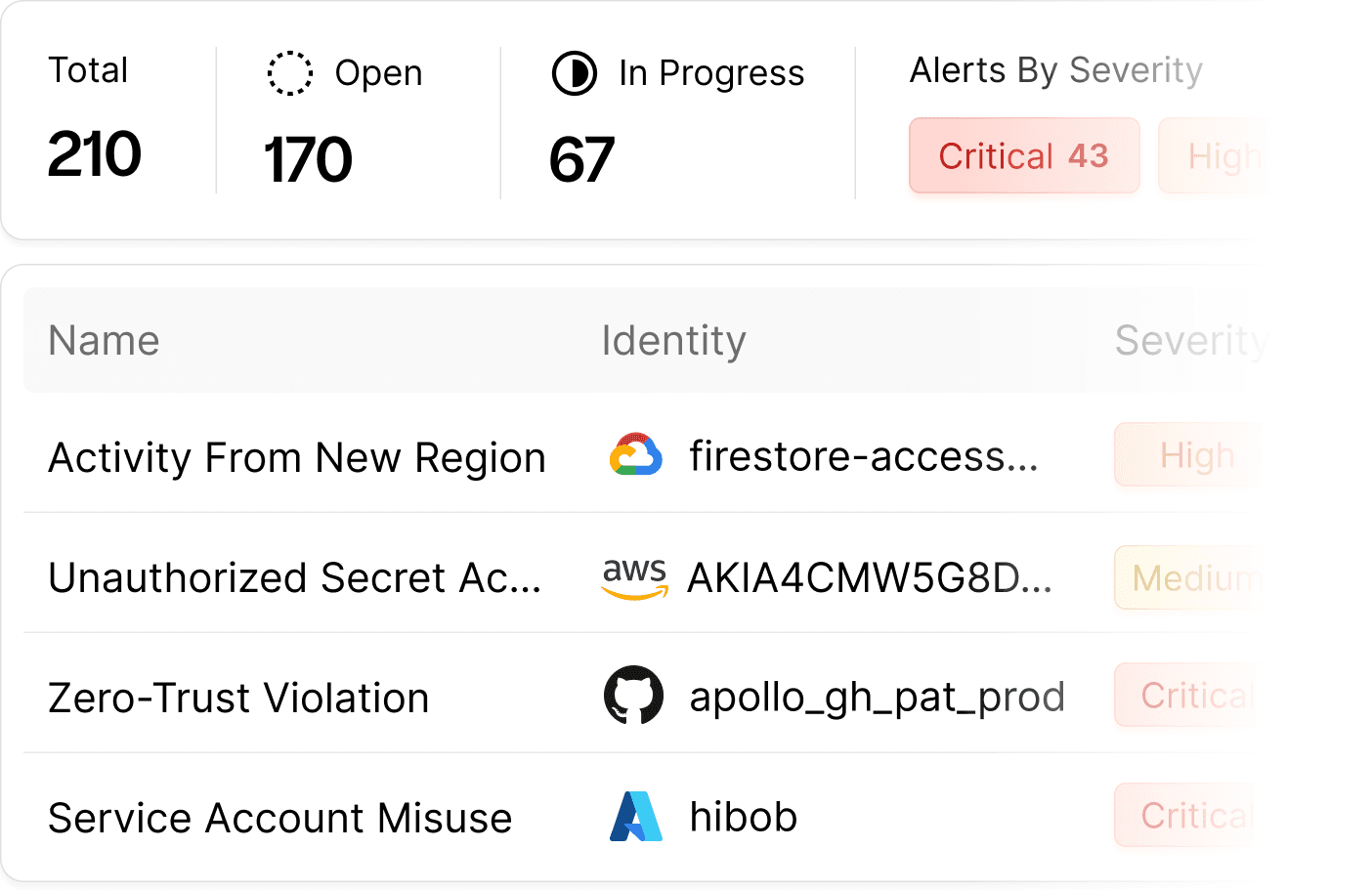
Precisely Detects Suspicious Activity and Responds in Real-Time
Clutch continuously monitors NHIs and analyzes behavior and access patterns over time to detect any unusual activity or deviation from established baselines. When an anomaly is detected, Clutch alerts the security team and provides tools for quick investigation and response to minimize potential damage.
Smoothly Integrates with the Organizational Workflows and Ecosystem
Clutch facilitates streamlined bi-directional integrations with existing workflows to deliver high-fidelity insights, recommendations, and alerts to leading SIEM, SOAR, SOC, and other automation tools - ensuring actionability, efficient operations, and minimized friction.

Non-Human Identity Security by Security Experts
Use Clutch with confidence and at scale