Visibility & Context
Clutch automatically discovers and correlates all NHIs into a contextualized inventory
The Challenge
The proliferation of Non-Human Identities across the entire enterprise, combined with their dynamic nature and decentralization, poses a major challenge for organizations seeking centralized and comprehensive visibility.
There is a critical need for a context-based inventory that allows security teams to understand which Non-Human Identities exist, their business context, where they are stored, who has access to them, their owners, and their level of privilege.
The Clutch Solution
Complete and Contextualized Visibility. Clear. Simplified.
Discovery
Continuously discover any NHI with no blind spots
Inventory
Catalog and correlate all NHIs across dispersed ecosystems
Context
Understand all NHIs through deep contextualization and enrichment
Clutch illuminates the entire spectrum of Non-Human Identities within the enterprise, offering unparalleled visibility through an in-depth inventory and detailed context enrichment.
Clutch provides an end-to-end visibility solution for all Non-Human Identities, including API keys, secrets, tokens, service accounts, and certificates across diverse landscapes.
Seamless Integration for NHI Data
Integrates seamlessly and gathers vital information from various systems and tools
This information is compiled into a comprehensive inventory of all NHIs and presented in a clear graph view, enabling security teams to understand their Non-Human Identity footprint across the enterprise.
With Clutch, you can finally see the full picture of your digital Non‑Human Identity ecosystem, enabling you to secure your NHIs everywhere.
Identity Lineage™: Comprehensive NHI Contextualization
Quickly understand the full context of any Non-Human Identity with Clutch's Identity Lineage™
Identity Lineage™ provides a contextualized view of any Non-Human Identity, offering detailed insights into how it operates and empowering security teams with a deep understanding of the organizational ecosystem through simple and intuitive visualization.
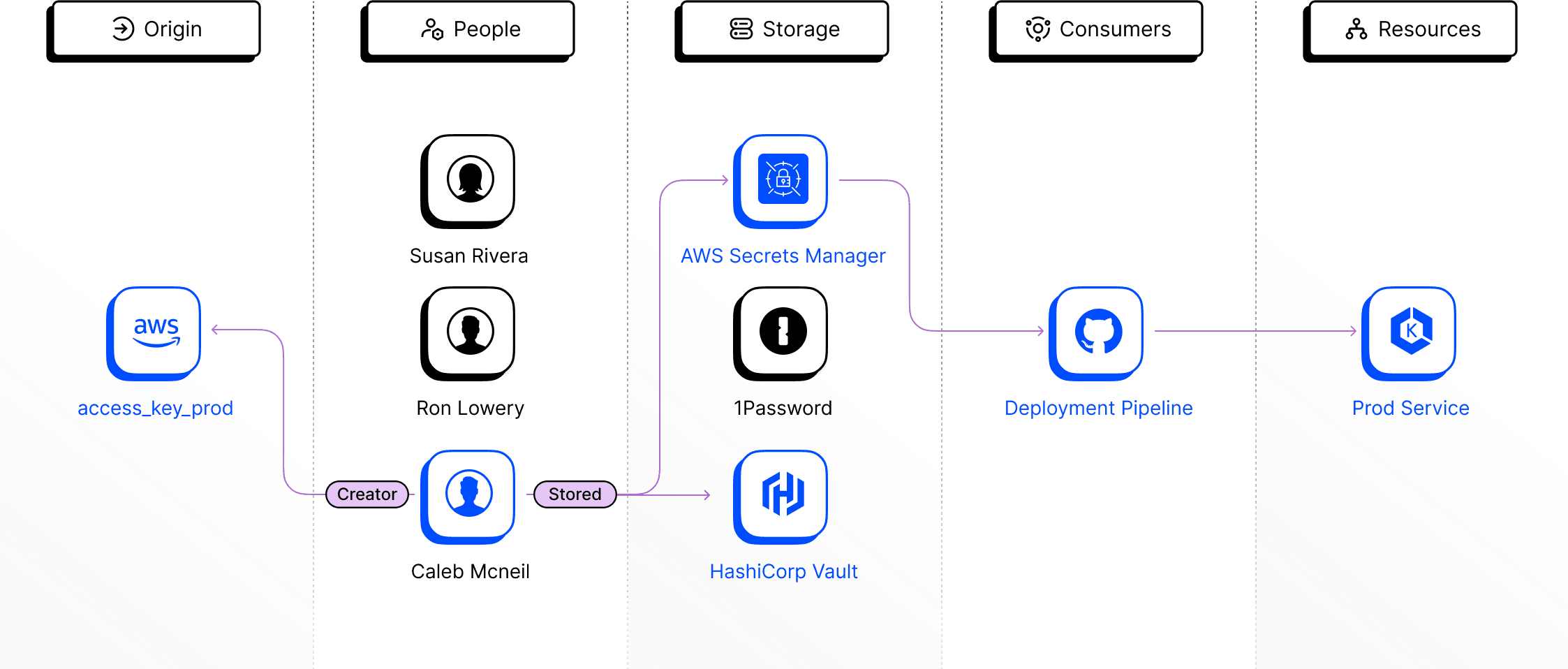
By aggregating and correlating information from various integrations, Clutch creates an intuitive visual mapping of the Non-Human Identity Lineage™. This allows security teams to quickly understand its full context:
Origin (Source of Truth)
Consumers (CI/CD Pipelines, Applications)
Attribution to the Workforce (Owners, Creators)
Resources (Access and Permissions)
Storage (Vaults, Password Manager, Code)
This NHI-centric contextual visibility enables not only the quick identification of involved parties and resources, but also provides security teams with the context they need to determine Which NHIs present an actual risk.
Unlock Tailored Insights Using Clutch's Powerful Query Builder
Tailored Data Consumption
Clutch's advanced query builder enables security teams to create multi-conditional queries with detailed granularity, allowing them to consume Clutch's contextualized inventory in the way that best suits their needs and workflows.
Flexible Breach Containment Options
Clutch facilitates a wide range of query options, enabling security teams to understand the potential impact of breaches, such as identifying unrotated NHIs from compromised applications, and covering various practices and scenarios.
Complex ecosystems, workflows, and technology stacks may require security teams to move beyond inventory lists and actively query data in more dynamic and flexible ways.