The widespread use of non-human identities (e.g. API keys, Secrets, Service Accounts) is causing security teams to evaluate the risks they create. In our last blog we reviewed the history of non-human identities and concluded that our risk management understanding of them lags far behind what's needed. Security professionals are used to setting policies and operational processes related to securing human identities, but NHIs are unfamiliar territory.
A reasonable next step in crafting a strategy for securing NHIs is to analyze exactly how they are different from human identities. Beyond clearly articulating why tools for human identities can't be applied to NHIs, this will help define the necessary characteristics for a workable approach. In this two-part blog we'll examine the differences between them, as the starting point for understanding how best to secure non-human identities.
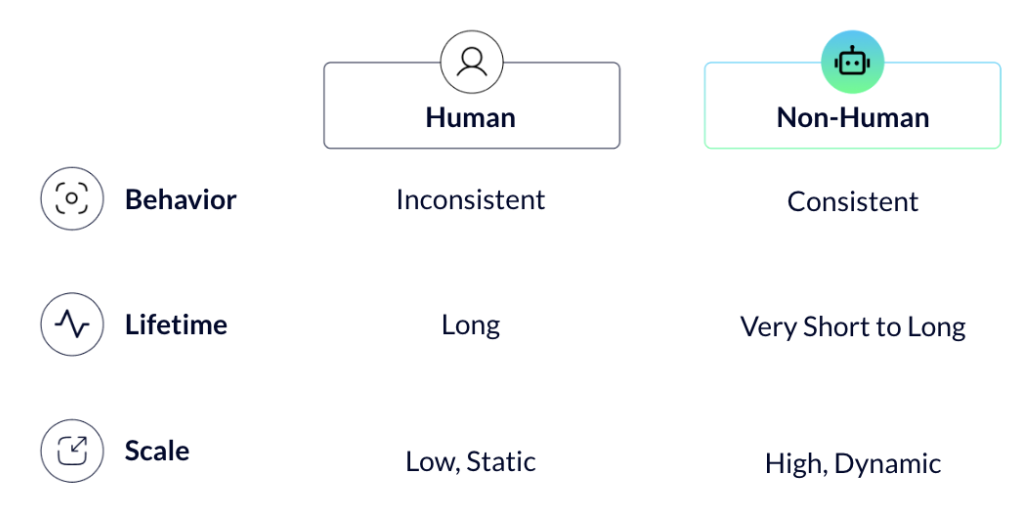
The Six Dimensions of Identity
Our comparison of human and non-human identities includes six attributes:
Behavior
Lifetime
Scale
Interaction
Responsible Organization
Threat Landscape
As we'll see, the two identity types vary widely across all these dimensions, necessitating a different approach to security controls. Let's start with the first three dimensions.
Behavior
The term “behavior” refers to how the identities' actions typically behave. Humans can be quite unpredictable: Their activities can vary considerably from application to application or across websites. For example, a person will interact with a sports website very different from a shopping site. They also may vary their location, time of day, location and endpoint device over time. Non-human identities however behave much more consistently, because they perform operations that are the result of code execution. The code was developed with methods and functions to do specific tasks, and will never do something which is beyond that very limited scope. So the behavior of NHIs will be much more predictable, limited, and consistent than human identities.
Lifetime
Human identities have relatively long lifetimes. They are created when people join the organization or begin a temporary engagement and are disabled or deleted when they leave. The typical human identity will last for years. NHI lifetimes are both much more varied, and ephemeral. Some identities may persist for a long time, but many others exist for no more than a matter of seconds.
Scale
In this dimension we're talking about the sheer number of identities to be managed and secured. Human identities never scale relatively high. You'll have your employees and temporary staff and that's about it. Furthermore, the number of accounts won't change drastically over time. NHI's are a totally different story: the number of identities is virtually unbounded, and because they are code generated and often ephemeral, they can scale up or down extremely quickly.
A Clear Pattern Emerges
Here's where we stand after evaluating three of the six dimensions: