As organizations scale their digital ecosystems, the number of machine identities—API keys, service accounts, tokens, certificates, and secrets—has skyrocketed. This surge has created significant security challenges and blind spots that attackers are increasingly exploiting. To address these challenges, security teams have turned to solutions like Non-Human Identity (NHI) Security and Cloud Infrastructure Entitlement Management (CIEM), especially as cloud adoption accelerates NHI proliferation. However, these two approaches serve distinct purposes. To build a resilient identity security strategy, it’s essential to understand how these solutions differ—and why NHI Security goes beyond CIEM.
While both aim to reduce risk and improve governance, they tackle different dimensions of identity and access management (IAM). NHI Security focuses on securing the ever-growing number of machine identities, while CIEM helps manage and optimize entitlements, particularly in cloud environments.
In this blog, we’ll break down the core differences, explore where their capabilities overlap, and explain why securing NHIs requires a broader approach—beyond what CIEM alone can offer.
NHI and CIEM: A Coupled Evolution in Cloud Security
Both CIEM and Non-Human Identity Security solutions protect cloud identities and may be coupled together in this context. However, while CIEM evolved to manage cloud entitlements, Non-Human Identity Security focuses on APIs, SaaS, on-prem, and CI/CD environments—areas where traditional CNAPP and CIEM solutions fall short.
This distinction highlights an important reality: CIEM and NHI Security are interconnected but serve different purposes. While CIEM enhances identity governance within cloud ecosystems, it does not address the broader and deeper security challenges posed by NHIs beyond the cloud.
This blog will break down these differences, providing security leaders with clear guidance on securing NHIs across hybrid and on-prem environments.
What Is Non-Human Identity Security?
Non-Human Identity Security focuses on protecting digital credentials used by machines, applications, and automated processes to authenticate and perform tasks within IT systems. Unlike human identities, which are tied to individuals, NHIs represent machine-to-machine interactions, including API Keys, Secrets, Tokens, Certificates, and Service Accounts.
These identities operate across diverse digital environments —cloud platforms, SaaS applications, on-prem systems, code repositories, CI/CD pipelines, data warehouses, and more.
Why NHI Security Matters
The sheer volume and complexity of NHIs have exploded in recent years, driven by trends like cloud-native architectures, DevOps automation, Microservices, and AI and machine learning workloads.
This rapid growth has outpaced traditional security tools, creating visibility gaps and increasing the risk of credential misuse. Unlike human users, NHIs can be created, modified, and decommissioned automatically—often without clear ownership or governance. This makes them a prime target for attackers, as compromised NHIs can provide persistent, unnoticed access to critical systems. NHI Security helps organizations answer critical questions like:
- How many NHIs exist in my organization?
- What’s their business context, and what purpose do they serve?
- What’s their level of privilege? Which NHIs have access to what resources?
- What risks do those NHIs pose for the business? Are there over-privileged service accounts, API keys, or tokens posing unnecessary risks? Where do stale permissions create vulnerabilities across cloud, SaaS, and on-premise environments?
Core Functions of NHI Security
- Centralized Visibility: Gain a comprehensive view of all NHIs across multi-cloud, SaaS, on-prem, and code environments.
- Lifecycle Management: Streamline machine credentials management from creation to decommissioning to prevent credential sprawl.
- Risk Reduction: Identify and prioritize diverse risks as overprivileged or stale NHIs and offer actional remediation strategies.
- Real-Time Threat Detection and Response: Continuously monitor for anomalous or suspicious behavior to detect threats early and respond swiftly.
- Zero Trust Enforcement: Apply Zero Trust principles, ensuring every NHI interaction is continuously validated and enforce least-privilege access policies.
What Is CIEM?
Cloud Infrastructure Entitlement Management (CIEM) platforms focus on managing cloud entitlements - permissions and access rights within cloud environments. These platforms analyze and optimize entitlements to ensure that users and non-human entities do not have excessive privileges or unnecessary permissions, thereby reducing the risk of security breaches caused by misconfigurations or over-provisioned access. CIEM helps organizations answer critical questions like:
- Who has access to what resources?
- Are there over-provisioned accounts?
- Where do unnecessary permissions create security risks?
CIEM tools analyze permissions across cloud platforms such as AWS, Azure, and GCP, identifying misconfigurations, enforcing the principle of least privilege, and reducing the risk of data breaches due to excessive access to sensitive information.
Why CIEM Is Essential
Cloud environments are inherently dynamic. Resources are spun up and down rapidly, users and services gain and lose access frequently, and managing permissions manually is impractical. CIEM helps mitigate these challenges by:
- Providing Entitlement Visibility: A clear map of who has access to what in the cloud.
- Automating Rightsizing: Continuously analyzing permissions to recommend and enforce least-privilege policies.
- Identifying Risks: Detecting dangerous permission combinations that could lead to privilege escalation or lateral movement.
However, CIEM’s focus is narrow—primarily dealing with cloud entitlements. It doesn’t cover NHIs operating outside cloud environments or provide comprehensive identity lifecycle management.
NHI Security vs. CIEM: Key Differences
While both NHI Security and CIEM aim to reduce security risks, their scope, depth of capabilities, and breadth of coverage differ significantly.
Solution Breadth - Coverage

In terms of solution breadth - coverage across different terrains, CIEM solutions are inherently limited to cloud infrastructure. This means that on-premise environments, SaaS apps, DevOps pipelines, and hybrid IT infrastructures often remain outside CIEM’s scope. NHI Security solutions, however, should be designed to be terrain-agnostic, providing unified visibility and control across all environments—whether cloud, on-premise, SaaS, or hybrid architectures.
Solution Depth - Capabilities
CIEM enforces the least privilege access in cloud environments, but it stops short of managing the full lifecycle, governance, and risk posture of NHIs—leaving critical security gaps. The table below highlights the key differences between the two solutions:
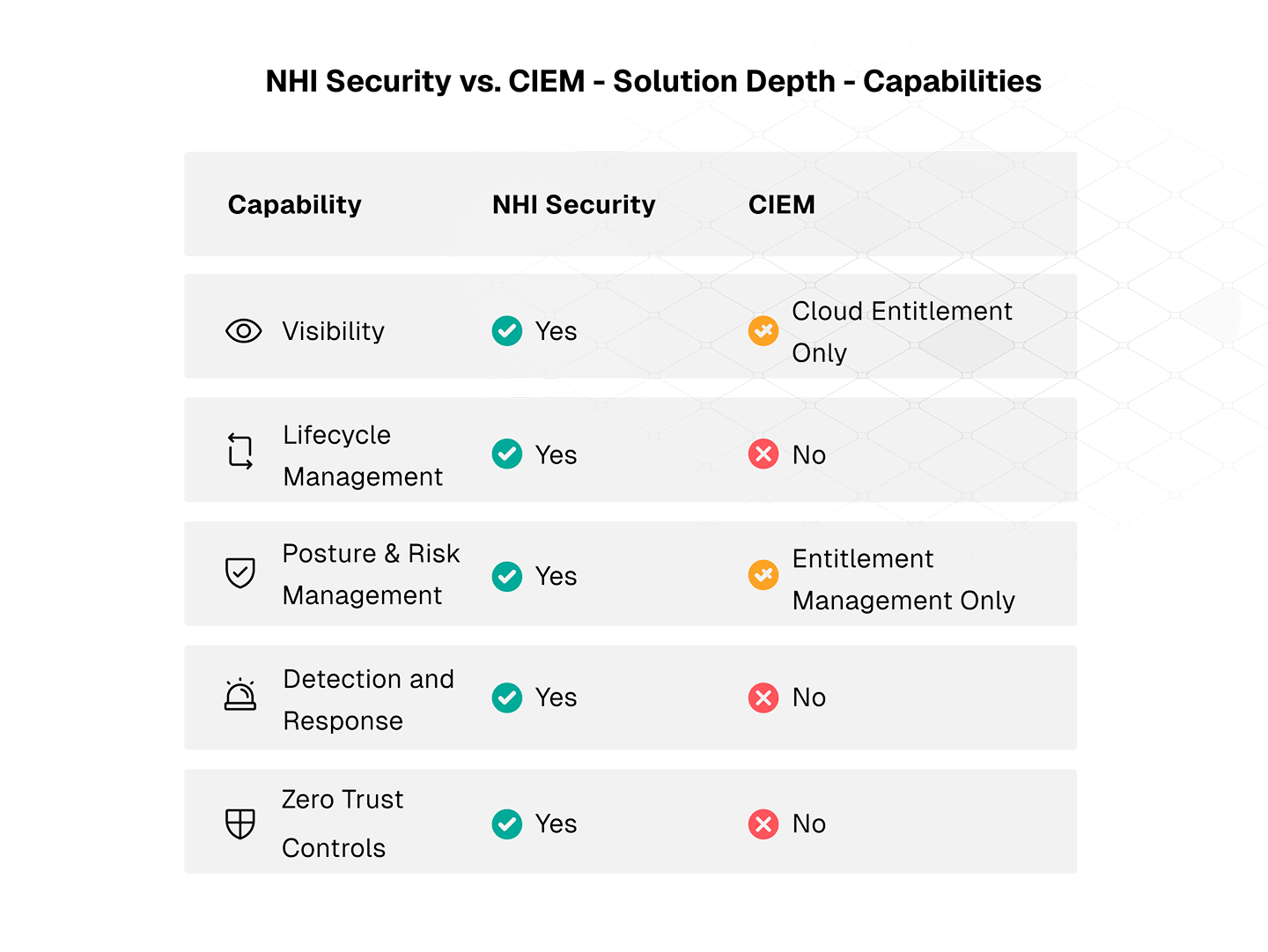
CIEM primarily focuses on managing permissions and entitlements within cloud environments, helping organizations identify overprivileged accounts, excessive permissions, and misconfigurations that could lead to security vulnerabilities. While this is a crucial aspect of security, CIEM does not extend its capabilities to securing NHI and machine identities that exist and operate beyond cloud platforms. NHI Security, on the other hand, provides a deeper and more comprehensive approach by addressing governance, lifecycle management, and continuous monitoring for all types of NHIs - both in the cloud and beyond.
Ultimately, while CIEM plays an important role in CSPM (Cloud Security Posture Management) by helping organizations manage cloud entitlements, NHI Security is a more holistic approach that ensures consistent governance and protection of machine identities across the entire IT ecosystem.
Why NHI Security Goes Beyond CIEM
While CIEM is critical for managing cloud entitlements, it doesn’t address the full spectrum of risks associated with NHIs. Here’s why organizations need NHI Security alongside CIEM:
- Broader Scope: NHIs operate across multi-cloud environments, SaaS applications, on-premises systems, CI/CD pipelines, and data warehouses. CIEM’s scope is limited to cloud entitlements, leaving gaps where NHIs exist beyond the cloud.
- Identity Lifecycle Management: Unlike CIEM, which focuses on permissions, NHI Security manages the entire lifecycle of non-human identities—from creation to decommissioning. This prevents credential sprawl and reduces the risk of stale, overprivileged NHIs lingering in the environment.
- Real-Time Threat Detection: CIEM tools lack real-time detection capabilities. NHI Security platforms continuously monitor NHI activity, detect anomalies, and trigger automated responses to prevent credential misuse or unauthorized access.
- Comprehensive Risk Coverage: CIEM addresses “who has access to what”, but NHI Security goes deeper—considering the context of identities, such as ownership, usage patterns, and potential risks tied to specific applications or workloads.
- Zero Trust Integration: NHI Security enables organizations to extend Zero Trust principles to NHIs, ensuring that every machine identity is continuously authenticated, authorized, and validated—no matter where it operates.
Real-World Example: Where CIEM Falls Short
Consider a scenario where an organization experiences a security breach due to a compromised API key embedded in a CI/CD pipeline. While CIEM may help identify cloud permissions tied to that API key, it won’t detect the compromised key’s activity within the CI/CD environment, nor will it manage its lifecycle or revoke access automatically.
This is where NHI Security excels—offering visibility into an API key’s creation, usage patterns, and associated risks while enabling real-time detection of suspicious activity. It also automates remediation, cutting response time from hours to minutes, and applies Zero Trust controls to thwart threats before they even emerge.
How Clutch Security Bridges the Gap
Security teams are overwhelmed by identity sprawl - an explosion of NHIs, unmanaged permissions, and increasing attack surfaces. Clutch delivers end-to-end NHI security, ensuring organizations regain control, reduce risk, and stop credential-based attacks before they happen.
- Comprehensive NHI Mapping: Clutch discovers and centralizes all NHIs across cloud, SaaS, on-prem, and DevOps environments. Its Identity Lineage™ provides deep context into each NHI’s origin, purpose, access patterns, and associated risks.
- Lifecycle Management: Enforces least privilege access and eliminates stale or over-privileged NHIs, reducing risk while improving operational efficiency.
- Efficient Risk Mitigation: Automated risk identification and prioritization ensure that security teams focus on the most critical threats. Predefined remediation playbooks streamline mitigation and minimize exposure.
- Real-Time Threat Detection: Continuous monitoring identifies credential misuse, abnormal behavior, and unauthorized access attempts—stopping breaches before they escalate.
- Zero Trust Enforcement: Clutch extends Zero Trust principles to NHIs, enforcing continuous verification, least privilege policies, and the elimination of long-lived credentials to prevent credential misuse.
Conclusion: NHI Security Complements, Not Replaces, CIEM
While CIEM is essential for managing cloud entitlements, it’s not enough to secure the growing number of Non-Human Identities operating across today’s complex IT environments. NHI Security provides the comprehensive, enterprise-wide coverage needed to manage and protect these critical assets.
Organizations that rely solely on CIEM may overlook significant risks tied to NHIs beyond the cloud. Integrating NHI Security with CIEM ensures a robust, holistic approach to identity security—reducing attack surfaces, enhancing governance, and supporting a modern, Zero Trust security model.
Ready to secure your NHIs beyond cloud entitlements? Let’s talk about how Clutch can help.