Compromised non-human identities—API keys, secrets, service accounts, certificates, and more — can be exploited by attackers in seconds, exposing enterprises to critical risks and devastating consequences. These identities, which often operate autonomously and hold highly privileged access, have fundamentally altered the security landscape.
Traditional security measures like secret rotation, long viewed as a cornerstone of credential management, are no longer sufficient. Even frequent rotations leave exploitable gaps, providing attackers with opportunities to strike between intervals.
While Zero Trust practices have become standard for human identities, the stakes are even higher for NHIs. The solution lies in adopting a Zero Trust framework tailored for NHIs, one that eliminates implicit trust and enforces continuous validation for every access request, regardless of its origin. Combined with ephemeral, auto-expiring identities, this approach not only fortifies security but also reduces operational overhead and enhances efficiency.
In our previous blog, we explored why NHIs are key to a Zero Trust strategy. In this blog, we’ll explore how Zero Trust principles can transform NHI security, the challenges with traditional approaches, and actionable strategies to implement a Zero Trust model that ensures only trusted entities gain access to your most critical resources.
Recap: What Is Zero Trust?
Zero Trust is a security model based on the principle of "never trust, always verify." Unlike traditional models that assume trust within a network perimeter, Zero Trust requires continuous verification for every access request, whether it originates inside or outside the network.

Core Principles of Zero Trust:
- Continuous Validation: Dynamically verify every access attempt based on context, such as identity, device, and location.
- Least Privilege Access: Grant entities only the permissions they need to perform their tasks—nothing more.
- Assume Breach: Operate under the assumption that breaches will occur, emphasizing swift detection, containment, and rapid response.
For NHIs, the equivalent principle is "Assume Leak," as secrets frequently end up unintentionally exposed on platforms like code repositories, package managers, and developer forums.
Why Zero Trust Matters: A Home Security Analogy
Imagine your home security. You wouldn’t assume that everyone inside is trustworthy just because they entered through the front door. Instead, you’d want to verify the identity and intent of anyone accessing sensitive areas, like a safe or personal belongings.
This analogy reflects the essence of the Zero Trust framework: trust no one implicitly, regardless of their origin, and continuously validate access requests based on context. For instance:
- A family member may need access to the living room but not the private office.
- A guest may be allowed into shared areas but requires explicit permission for other spaces.
- Even a previously trusted individual might need re-verification over time.
In the context of NHI security, this means verifying every access attempt dynamically—whether it originates inside or outside your network. This approach ensures that only verified, authorized entities can access resources, and only for the specific purposes they’re permitted to. By applying Zero Trust principle to NHIs, organizations can drastically reduce the risk of unauthorized access, even if credentials are leaked or malicious actors are already inside the network.
Challenges with Other Security Models
Traditional approaches to identity security fall short when applied to NHIs. Legacy identity and access management (IAM) systems, designed for human identities, and practices like secret rotation have proven as insufficient and even dangerous as they creates a false sense of security. Those methods fail to meet the demands of NHI security in today’s fast-paced, multi-cloud and multi-terrain environments. Let’s explore why:
1. The Limitations of Traditional IAM
IAM systems were built for human identities, relying on static credentials and rigid access controls. NHIs introduce complexities that these systems cannot effectively address:
- Static Secrets as Vulnerabilities: NHIs—such as API keys, service account tokens, and certificates—often rely on long-lived static credentials. If exposed, these credentials grant attackers continuous access, enabling lateral movement and data theft.
- Limited Visibility: Traditional IAM tools lack mechanisms to monitor NHI activity at scale, leaving organizations unaware of lifecycle changes, excessive permissions, or misuse.
- Overprivileged Identities: To prevent workflow disruptions, NHIs are often given excessive permissions. This overprovisioning creates a significant attack surface, amplifying the impact of a breach.
In an era of increasingly sophisticated threats, static and manual IAM processes are too slow to protect dynamic NHIs effectively.
2. Secret Rotation: A Misleading Safety Net
While secret rotation has long been considered a security best practice, it’s increasingly evident that this approach is insufficient for addressing modern threats. In reality, secret rotation can become a ticking time bomb, failing to safeguard organizations in critical ways:
- Exploitation Windows: Secrets are rotated periodically, creating exploitable gaps between rotations. Fast-moving attackers can compromise and misuse credentials during these windows.
- No Real-Time Validation: Rotations don’t solve the fundamental issue of verifying the legitimacy of credential use in real time, allowing malicious actors to operate undetected.
- Operational Strain: Frequent secret rotations create significant downtime risks, disrupt workflows, and drain IT and DevOps resources. These inefficiencies divert attention from core business initiatives.
The result? A False Sense of Security. Relying on rotation alone may lead organizations to underestimate the importance of proactive monitoring, dynamic access control, and continuous validation. The inherent limitations of secret rotation make it ill-suited for the fast-paced, high-stakes world of NHI security.
Pro Tip: Check out our research exposing the flaws of secret rotation and see how attackers exploit secrets faster than ever before.
Example: API Key Exposure in a Public Repository
Imagine this: An organization's developer mistakenly uploads an API key with admin privileges for a cloud environment to a public GitHub repository. Within minutes, attackers discover the exposed key using automated scanning tools.
Traditional Security Methods:
- Secret Rotation: If the organization follows a secret rotation policy, the API key may be set to rotate every 90/60 or even 30 days. This provides a huge exploitation window. An attacker can use the exposed key to launch attacks immediately, such as creating malicious virtual machines or extracting sensitive data, well before the next rotation occurs.
- Static Network Controls: IP whitelisting or firewall rules may be in place, but they are ineffective if the attacker operates from an allowed network range or uses VPNs to spoof legitimate locations.
Zero Trust Approach:
In a Zero Trust architecture, API key access is governed by dynamic, context-aware policies that continuously validate requests. By leveraging behavioral anomaly detection, Zero Trust systems identify unusual access patterns, such as new IP addresses, unexpected geographic locations, or excessive API calls. Anomalous requests are flagged or blocked in real time.
The outcome? In this scenario, the Zero Trust approach mitigates damage immediately: The suspicious key consumption attempt is restricted. The anomalous activity may trigger alerts for investigation, allowing security teams to respond before data is compromised. Furthermore, the stolen key is either invalidated or severely restricted in scope. Unlike rotation, which leaves a time gap for exploitation, Zero Trust minimizes or eliminates exploitable windows through continuous validation.
Implementing Zero Trust for NHIs
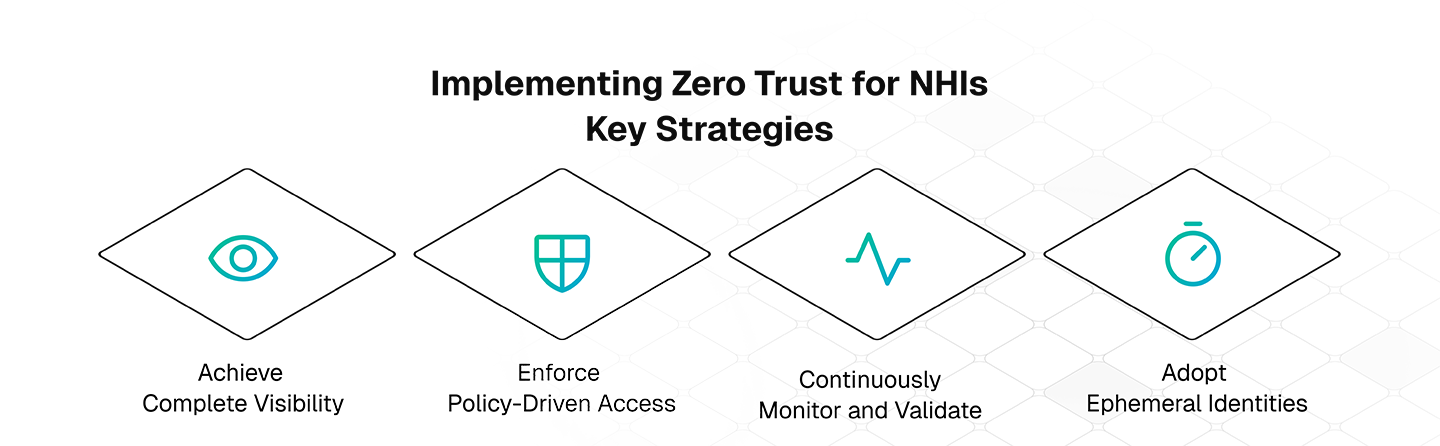
Transitioning to Zero Trust for NHI management involves several key strategies:
1. Achieve Complete Visibility
Build a contextualized inventory of NHIs across cloud, SaaS, and on-prem environments. Platforms like Clutch offer insights into each NHI’s origin, associated people, storage, consumers, and resource access. This inventory serves as the foundation for NHI lifecycle tracking, risk identification and remediation, and anomaly detection.
2. Enforce Policy-Driven Access
Leverage identity providers to enforce granular, policy-driven access controls. Ensure every access attempt is validated against dynamic conditions, such as the requesting service’s identity and the sensitivity of the target resource.
3. Continuously Monitor and Validate
Real-time monitoring detects unauthorized activities, while continuous validation ensures NHIs remain trusted and prevents compromised NHIs from being exploited.
4. Adopt Ephemeral Identities
Replace static credentials with short-lived access tokens generated dynamically by tools like AWS IAM Roles, Azure Managed Identities, and GCP Workload Identity Federation. This approach minimizes the attack surface while aligning with Zero Trust.
Benefits of Zero Trust for NHI Security
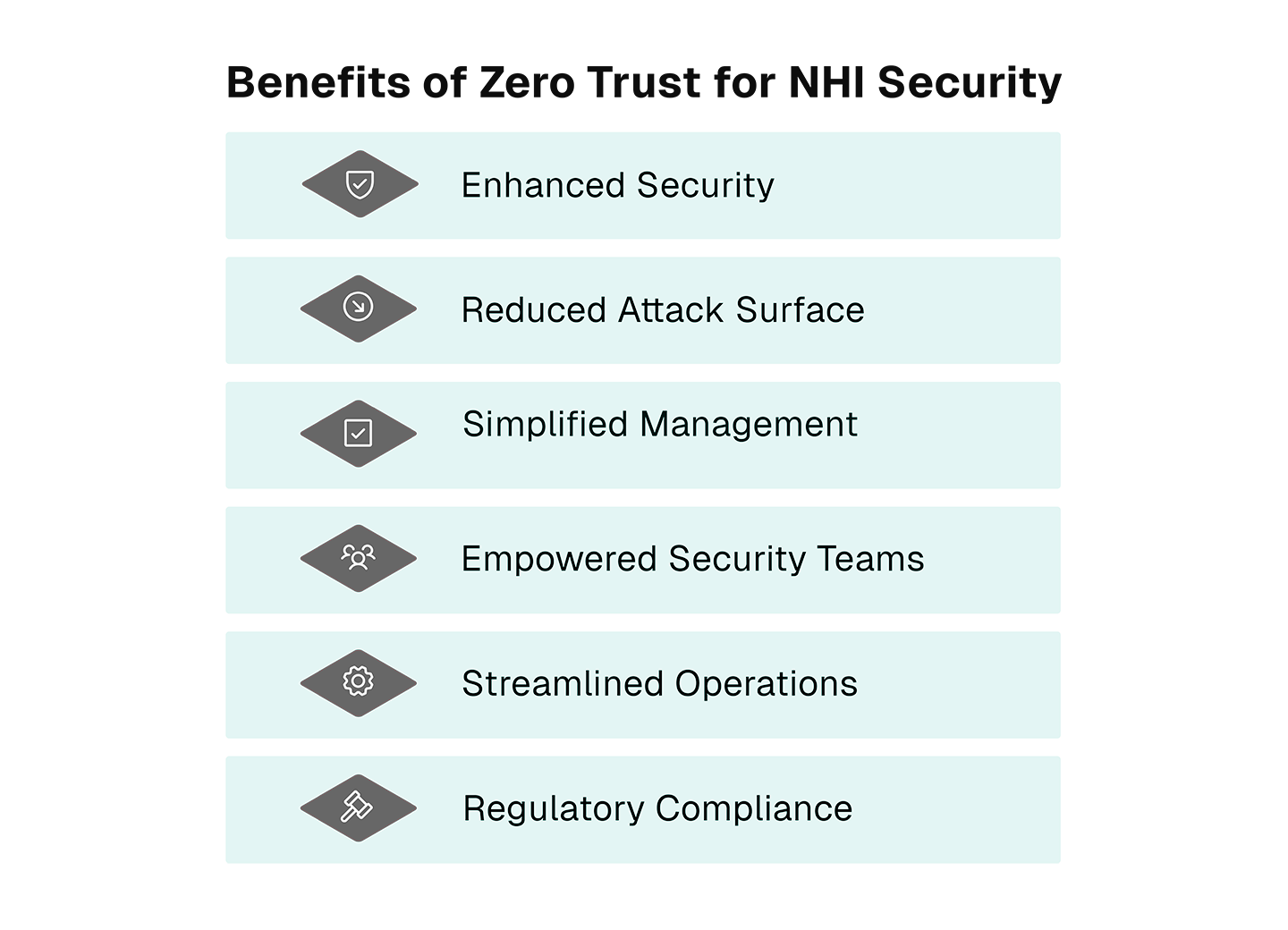
- Enhanced Security: Continuous validation and ephemeral identities dramatically reduce the risk of credential misuse, ensuring only verified entities gain access.
- Reduced Attack Surface: Short-lived credentials and least privilege access significantly limit the impact of potential breaches.
- Simplified Management: Automated processes and centralized monitoring alleviate the operational overhead associated with manual credential management and frequent rotations.
- Empowered Security Teams: Removes dependency on IT and DevOps for credential management and rotations, freeing teams to focus on strategic priorities and core responsibilities.
- Streamlined Operations: Maintains five-nines uptime, enhancing agility and preventing operational disruptions caused by rotation schedules.
- Regulatory Compliance: Adheres to GDPR, NIST, and CCPA requirements through robust identity governance and secure access controls.
To conclude: Zero Trust is no longer a nice-to-have—it’s essential for securing NHIs in today’s dynamic, multi-cloud environments. By adopting principles like continuous validation, least privilege access, and ephemeral identities, enterprises can significantly enhance their security posture while reducing operational complexity.