We Deliberately Exposed AWS Keys on Developer Forums: Attackers Exploited One in 10 Hours
When Help Turns Hazardous: AWS Keys and Developer Forums
A cry for help can become a gift for attackers.
Just one misplaced snippet. That’s all it takes to turn a harmless developer question into an open invitation for attackers — or curious strangers. While it’s rare for developers to knowingly include secrets in forum posts, accidents happen. A misstep in sharing code or an oversight in sanitizing a snippet can expose critical information. Our experiment wasn’t just about the frequency of such leaks; we sought to understand the ferocity with which attackers—and even well-meaning strangers—scan these platforms for opportunities, no matter how rare.
This is the fourth blog in our ongoing series, where we expose the limitations of traditional secret rotation and how attackers exploit leaked secrets. If you’re just joining us, we recommend starting with our Prelude, which outlines the motivations behind this research and provides a high-level summary of the risks involved.
So far, we’ve explored Code Hosting & Version Control Systems, Package Managers, and Code Sharing Platforms. In this installment, we focus on developer forums — platforms designed for community collaboration that can inadvertently become hotspots for accidental leaks.
Attackers in the Threads: The Dark Side of Developer Discussions

Scenarios
In the table below, we have listed all the scenarios we executed across various developer forums and communities to observe how quickly exploitation would occur and to gauge user responses upon seeing those secrets.
| Website | Scenario Name | Description |
| Secrets Overflow | Posted a question on Stack Overflow including an AWS access key. | |
| Quora Quandary | Posted questions on Quora, accidentally leaving an AWS access key exposed in formatted text. | |
| Quora Quandary 2 | Posted questions on Quora with an AWS access key exposed in plain text. | |
| Someone Obviously Reddit | Posted in various Reddit subreddits including an AWS access key in the posts. | |
| Special Delivery! | Opened a topic on the Postman Community forum including an AWS access key. |
Results
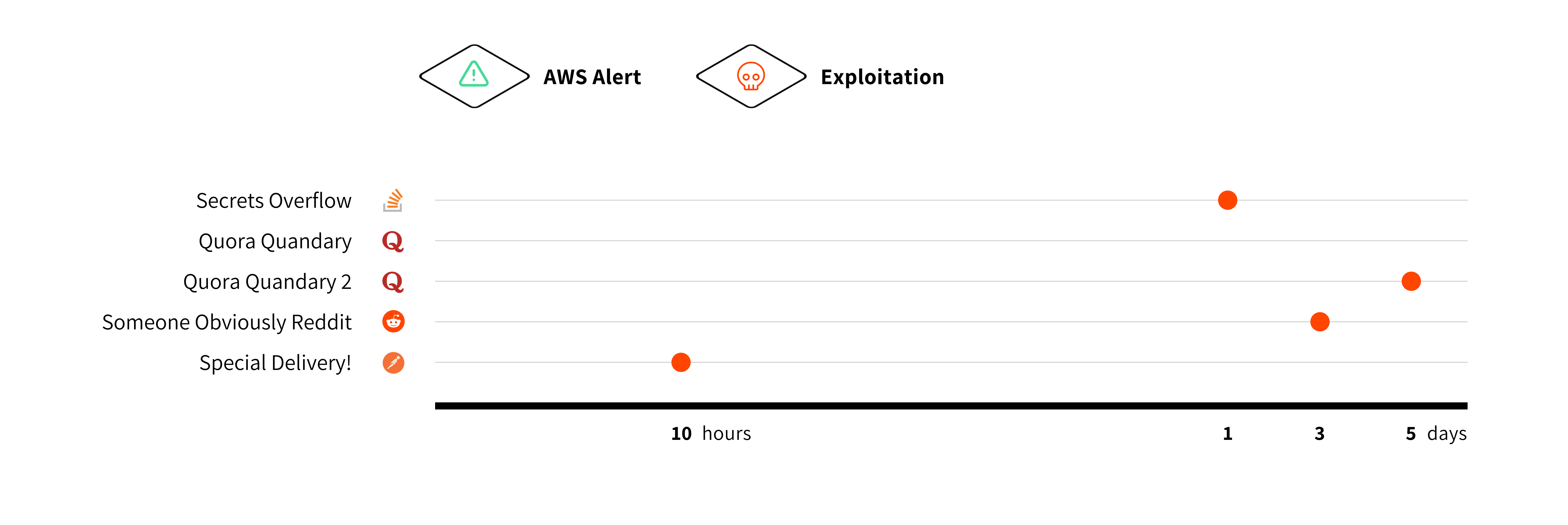
Our experiment revealed that while developer forums like Stack Overflow, Quora, Reddit, and Postman Community are invaluable for collaboration, they are not immune to exploitation when secrets are accidentally leaked.
On Stack Overflow, a secret was exploited within a day, while a plain-text secret on Quora took five days to be compromised, likely by a human rather than automated scanners. Reddit saw exploitation within three days, and the fastest compromise occurred on Postman Community, where a secret was exploited in just ten hours.
Despite slightly longer exploitation times compared to repositories, the risks are no less severe, as these public platforms often fall outside enterprise monitoring, leaving good samaritans or moderators as the only defense.
| Platform | Scenario | Time to Exploit | Time to Alert ⚠️ |
| Secrets Overflow | 1 day | No Alert Sent | |
| Quora Quandary | No exploitation | No Alert Sent | |
| Quora Quandary 2 | 5 days | No Alert Sent | |
| Someone Obviously Reddit | 3 days | No Alert Sent | |
| Special Delivery! | 10 hours | No Alert Sent |
“Sir, I Think You Dropped Something”: The Scenarios We Tested
Stack Overflow Scenarios
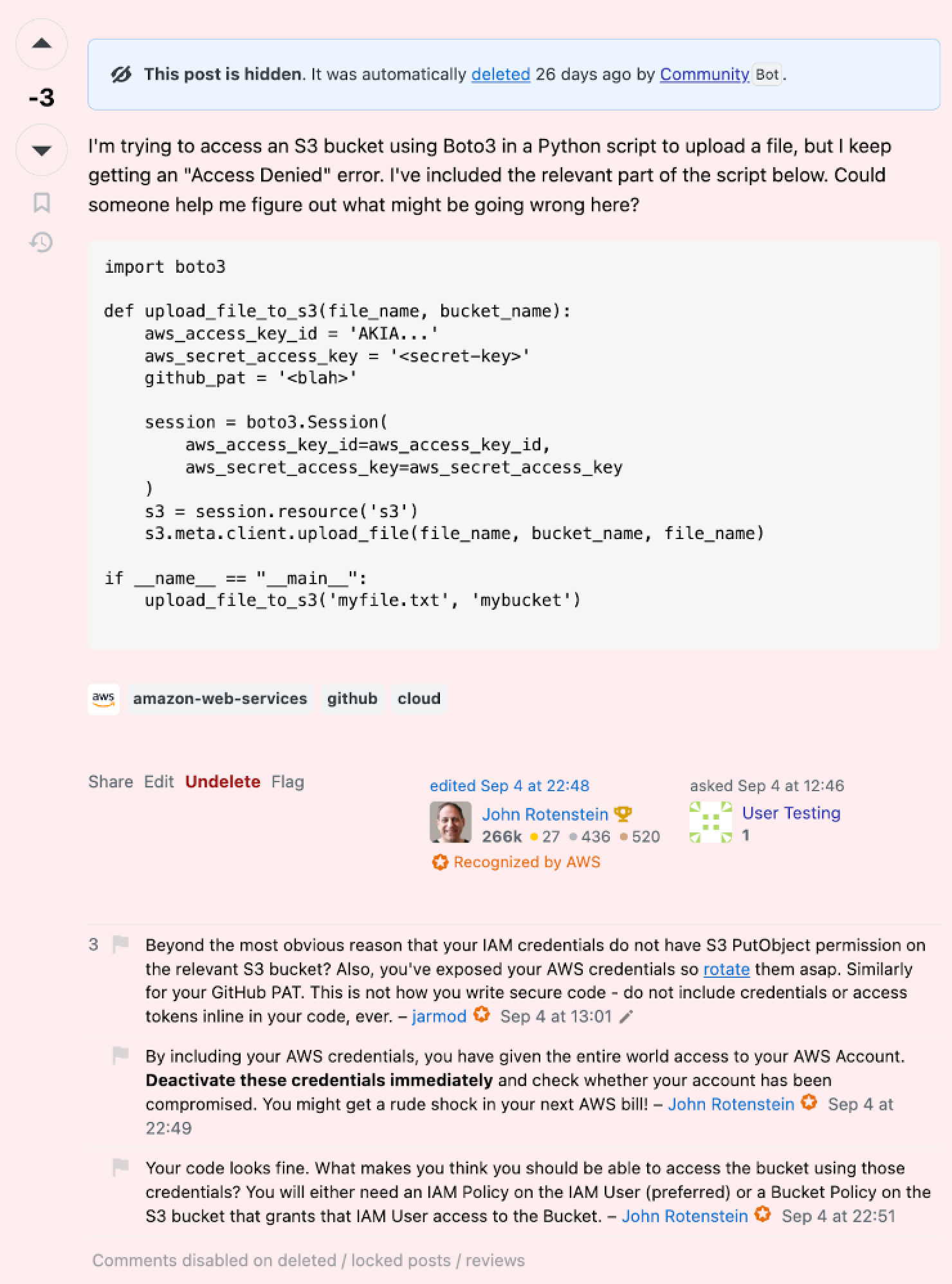
Secrets Overflow
We intended to ask a question in Stack Overflow about why we were getting an 'access denied' error when trying to upload a file, but it seems we accidentally left our key in the post. Oops!
| Exploited? | Exploitation Time | Alert Time |
| Yes | 1 day | No alert sent |
We received no email from AWS about the key exposure, which makes sense. Within a single day, however, our key was exploited. Are attackers lurking on Stack Overflow, or were there curious users poking around? It’s hard to say. Several good samaritans urged us to quickly revoke the keys, and a moderator eventually deleted our post.
Quora Scenarios
Quora Quandary
We posted some questions to the Quora community, accidentally leaving our key exposed.
| Exploited? | Exploitation Time | Alert Time |
| No | - | No alert sent |
We observed no hits on thiskey, suggesting that Quora may rarely be scanned. Why rarely? See the next scenario, where we observed something different.
Quora Quandary 2
We posted the same questions to the Quora community, but this time we left our key in plain text without any formatting.
| Exploited? | Exploitation Time | Alert Time |
| Yes | 5 days | No alert sent |
The fact that we observed a hit on this key only 5 days after publishing suggests the exploitation was potentially performed by a human or an infrequent scanner. Interestingly, while the formatted secrets scenario saw no hits,thisone did.
Reddit Scenarios
Someone Obviously Reddit
We posted a few times in various subreddits to see what would happen with our secrets on Reddit.
| Exploited? | Exploitation Time | Alert Time |
| Yes | 2 days | No alert sent |
Our secret was picked up within 3 days, and a kind stranger informed us that we shouldn’t do that. Lesson learned.
Postman Community Scenarios
Special Delivery!
We opened a topic on the Postman Community with an AWS access key, suspecting that some prying eyes might pick up our secret.
| Exploited? | Exploitation Time | Alert Time |
| Yes | 10 hours | No alert sent |
Within 10 hours, someone did. The topic remainsactive.
What’s Next
With Code Hosting & Version Control Platforms, Package Managers, Code Snippets & Sharing Platforms, and now - developer forums covered, our next post will explore a scenario inspired by the high-profile Internet Archive breach, where attackers exploited an exposed configuration file to access sensitive credentials. By mimicking this breach, we demonstrated firsthand that this incident wasn’t a one-off event. It serves as a warning to organizations everywhere: a single exposed token can cascade into far-reaching consequences.
If you can’t wait for the next blog post, we invite you to download the full report, with all scenarios we ran, a deeper dive into our methodologies, platform-specific insights, attacker behavior patterns, and the tool we built to neutralize exposed secrets instantly. It’s an essential read for any organization looking to secure its systems against the escalating risks of exposed secrets.