TL;DR:
Secret rotation is a legacy security practice rooted in compliance rather than effectiveness. In today's world, attackers can exploit exposed secrets within seconds, rendering rotation inadequate as a proactive security measure. Frequent rotations add operational overhead, create friction between teams, and provide a false sense of security. Modern security demands a shift toward Zero Trust, context-aware access, and ephemeral solutions to truly mitigate risk. Read below how it all started, and what's a more modern and effective approach to securing NHIs.
Introduction: The Origins of Secret Rotation
The practice of regularly rotating secrets has become a default part of many organizations' security protocols. Dating back to the 1970s, early systems like MULTICS implemented password expiration to combat issues such as password sharing and shoulder surfing. Compliance requirements like PCI DSS further mandated frequent encryption key rotations to limit the impact of compromised data. Eventually, this concept extended beyond user passwords to encompass API keys, tokens, and other non-human identities. However, while secret rotation has historical roots in compliance, its effectiveness as an ongoing security measure is worth a critical re-examination.
Rethinking Security from First Principles
To understand the value—or lack thereof—of frequent secret rotations, we need to return to first principles. Every security measure should address a specific threat effectively, with minimal operational impact. Secret rotation emerged to mitigate risks in environments with limited automation, where it was relatively straightforward. However, with the rise of cloud computing, SaaS, and distributed architectures, managing secret rotations has become more complex. Moreover, most secrets today are internet-facing, increasing the risk of exposure. We must ask whether the original reasoning behind secret rotations still holds or if the practice has become more of a compliance checkbox than an effective security measure.
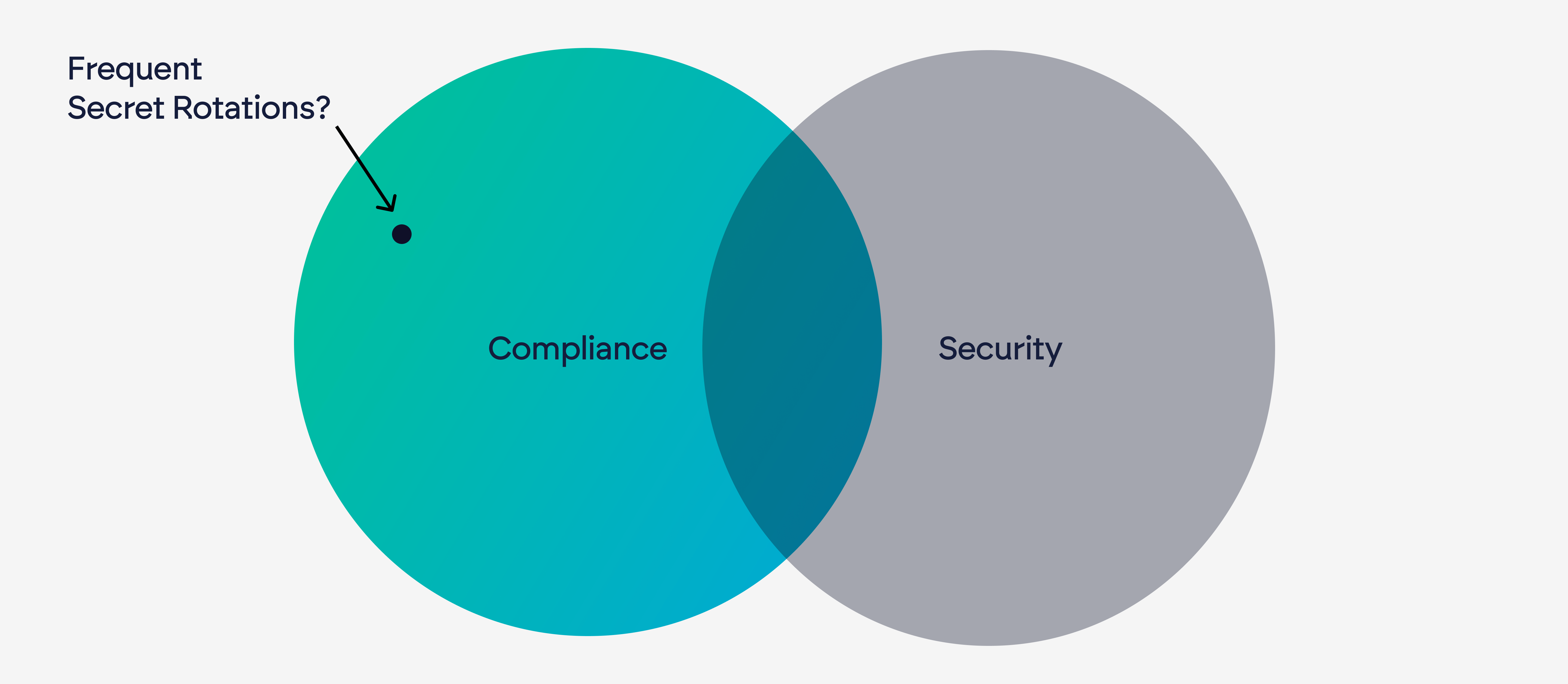
The Security Limitations of Frequent Secret Rotations
Exploitation Within Valid Windows: Attackers today are highly efficient. Once a secret is compromised, it is often exploited within minutes, sometimes seconds. Even with a 24-hour rotation window, an attacker has plenty of time to cause damage. According to Cybenari's blog post 'What's the Worst Place to Leave Your Secrets?', intentionally leaked secrets were accessed by malicious actors within 120 seconds of being made public. This rapid response time highlights the futility of relying on rotation alone—attackers do not need much time to exploit a vulnerability.
False Sense of Security: The act of rotating secrets can give organizations the illusion of safety. If attackers can exploit a secret immediately after compromising it, rotation does little to prevent breaches. This false sense of security often leads to complacency, with organizations failing to implement more robust security measures like real-time monitoring and zero trust. The incidents involving CircleCI and Sisense showed that even weekly rotations did little to help once secrets were already compromised.
Operational Challenges and the Cost of Rotations
Increased Friction and Overhead: Frequent secret rotations require careful synchronization between security and engineering teams, leading to slowed development cycles and misconfigurations. The operational cost of each rotation, including testing and updating dependencies, creates significant burdens on engineering resources. This overhead results in a dependency cycle, where security teams rely on engineers, distracting them from core product work.
Resource Intensive: Rotations are not only cumbersome but are also resource-intensive. Each rotation cycle demands that engineers propagate updated secrets across systems, ensure dependencies are properly configured, and verify system stability. This ongoing operational burden increases the likelihood of human error, further undermining security.
A Reactive Measure, Not a Proactive Solution
Frequent secret rotation is best understood as a reactive measure to mitigate the impact of an already compromised secret—similar to resetting a password after a known breach. As OWASP points out, rotating secrets can reduce the risk associated with stolen credentials, but relying on rotation as a proactive defense is misguided. NIST's updated guidelines advise against frequent password changes without evidence of compromise; the same logic applies to secrets—if a secret has not been compromised, rotation offers no inherent benefit and often creates more risks than it mitigates.
The Path Forward: Zero Trust and Ephemeral Solutions
The traditional approach to secret management, including frequent rotations, falls short in today’s dynamic environment. To effectively secure NHIs, organizations need more adaptive solutions—ones that leverage Zero Trust principles and ephemeral credentials. Zero Trust operates on the principle of "never trust, always verify," demanding strict identity verification for every access attempt. Ephemeral secrets eliminate the need for long-term static credentials, reducing the risk window to near zero.
Solutions like Clutch employ Zero Trust principles to handle NHIs based on operational context and risk. By shifting from static secrets to dynamic, context-aware controls, organizations can minimize the risks associated with compromised credentials. Going ephemeral, where secrets have extremely short lifespans and are generated as needed, offers a proactive path forward, allowing for secure access without the operational headaches of frequent rotations.
Conclusion: A Modern Approach to Security
The time has come to replace outdated practices like frequent secret rotations with proactive, context-aware security measures. By adopting Zero Trust and ephemeral identity solutions, organizations can better secure their systems, reduce operational burdens, and eliminate the false sense of security that rotations bring. Modern security must be about more than compliance checkboxes—it should proactively protect systems in an evolving threat landscape, empowering security and engineering teams to focus on innovation.