The unsung heroes of modern automation—Non-Human Identities—are quietly running the show. From service accounts managing backups to API keys powering integrations, NHIs are the digital backbone of IT. But like an unmonitored factory, their rapid proliferation across cloud, SaaS, on-prem, and hybrid environments often comes with excessive privileges. This makes NHIs both operational MVPs and potential security risks.
Many security teams today struggle to answer even the most basic questions about the NHIs in their ecosystem:
- Which NHIs even exist to begin with?
- What’s their business context, and what purpose do they serve?
- Where are they being stored?
- Who are their owners?
- Which NHIs are not needed anymore?
And beyond those basic questions that revolve around operational aspects, security is an important aspect as well, which raises these questions:
- What’s their level of privilege?
- Who can access and use those NHIs?
- What risks do those NHIs pose for the business?
- Would we know if any of those NHIs is compromised?
Answering these questions holistically—across the entire enterprise—is no small feat. And make no mistake: mismanaging NHIs can lead to catastrophic breaches. Complete and continuous visibility and detailed context are the twin pillars of a secure NHI strategy, as the Cloudflare Thanksgiving 2023 incident demonstrated all too painfully. Following the Okta breach of October 2023, Cloudflare neglected to rotate a few credentials mistakenly believed to be dormant—an oversight caused by limited visibility and context. The result? A holiday with more “stuffing” than anyone wanted.
Visibility Alone Won’t Save You
First things first: you need a comprehensive inventory of NHIs. This means tracking them across clouds, SaaS platforms, CI/CD pipelines, and even obscure data warehouses. Every token, secret, certificate, API key, and service account needs to be identified and cataloged. But if visibility is the map, then context is the legend—and without context, your map might as well be blank.
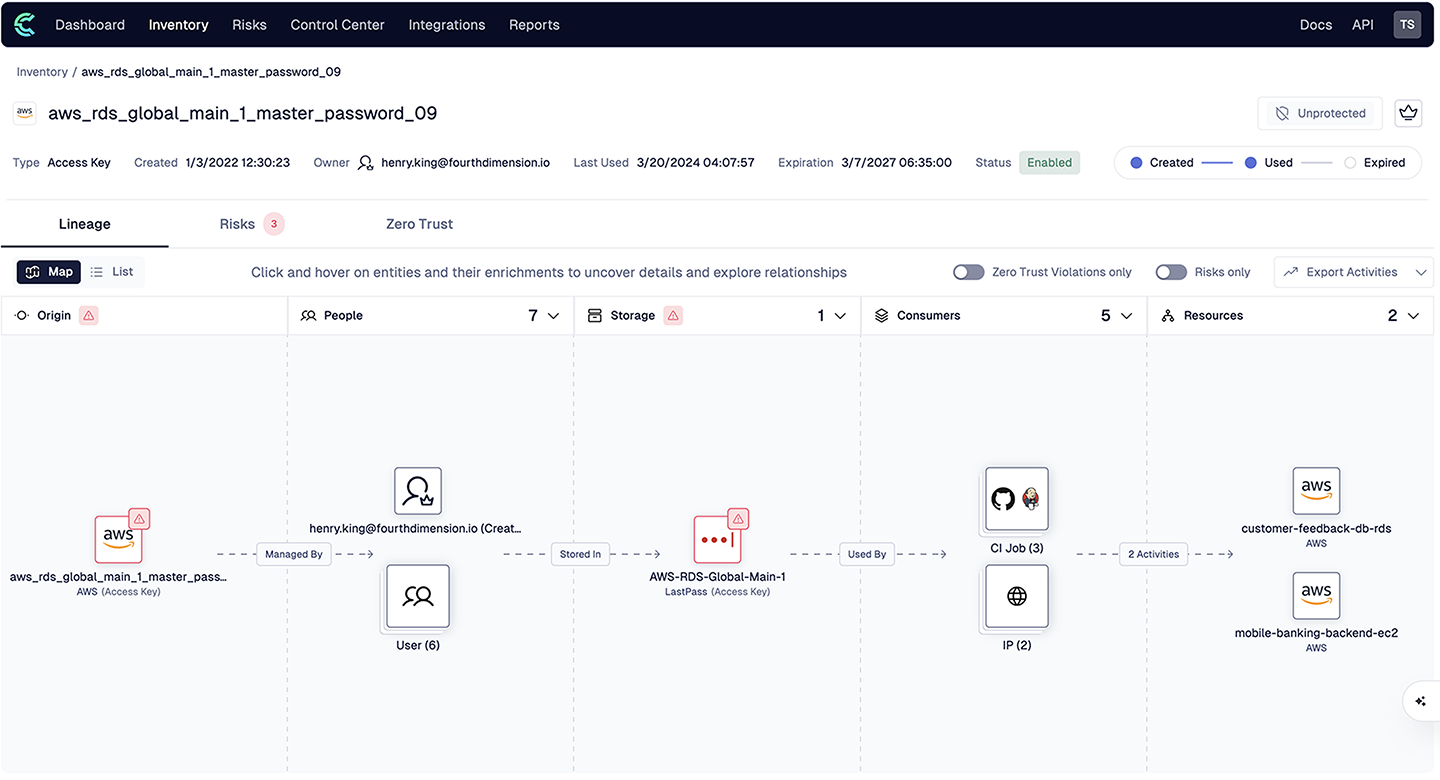
However, to truly secure NHIs, organizations need full context. Enter Clutch’s Identity Lineage™ — a breakthrough approach that provides a comprehensive map of every NHI’s lifecycle, relationships, and dependencies. Think of it as a family tree for your digital workforce, including your IT stack, your employees, your workloads, and your data Identity Lineage™ is broken down into the following components:
- Origin (the NHI’s authoritative Source of Truth): Where the NHI was created, its type, and other key information.
- People (Attribution to the Workforce): Who created, owns, or manages it, and who in the workforce can access it.
- Storage: The locations where credentials are stored—whether their vaults or secret managers, password managers, or even hardcoded in code.
- Consumers: The entities, applications or systems utilizing the NHI for inter-service operations, enriched with details like geo-location or SaaS vendor identification.
- Resources: The resources or data the NHI grants access to when used, and the nature of these interactions.
After composing the Identity Lineage™, the relevant risks (if any) are layered on top of every component in the lineage, to highlight areas of interest and risk.
Armed with this crucial information, Identity Lineage™ not only visualizes the complete ecosystem of every NHI, but it also pinpoints dormant or over-privileged NHIs but also automates workflows to ensure security compliance, reduce attack surfaces, and simplify operations.
Real-World Scenarios
Identity Lineage™ provides actionable intelligence by mapping and understanding diverse context parameters, enabling swift risk identification and resolution. Coupled with advanced query options, it elevates security teams' efficiency in addressing issues. For example:
- Mapping Associated People: Quickly identifies offboarded employees, allowing their NHIs to be decommissioned promptly.
- Mapping Sources: Pinpoints which NHIs require rotation or decommissioning in response to third-party breaches, reducing the risk of supply chain attacks.
Here are some practical examples of Identity Lineage™ in action and the critical insights it delivers:
- The Wandering API Key: A contractor-created API key remained active for two years, still in use by an external application. Using Identity Lineage™, the security team traced its origin, enabling swift deactivation and the implementation of time-limited credentials.
- The Rogue Service Account: Malware exploited an administrator-privileged service account originally created for a deprecated project. Identity Lineage™ identified its origin, underscoring the dangers of unmonitored NHIs.
- The Stale Access Key: An AWS access key, unused for three years, was flagged as stale. Worse, it was stored in a password manager rather than a secure secrets manager, amplifying its risk profile.
Why Identity Lineage™ is the Cornerstone of NHI Security
Identity Lineage™ is more than a tool—it’s a strategic enabler for actionable intelligence across several critical areas, unlocking advanced capabilities that transform how organizations manage NHIs:
- Efficient Lifecycle Management: Pinpoint stale NHIs for decommissioning or manage NHIs appropriately at various stages of their lifecycle.
- Enhanced Risk Mitigation: Quickly identify dormant or over-permissioned identities, reducing the likelihood of risks escalating into active threats.
- Swift Detection & Response: Identify identities tied to potential breaches, whether from a compromised vendor in a supply chain attack or unusual consumption patterns from unauthorized geolocations.
- Smart Zero Trust Architecture: Enable continuous validation of each NHI’s usage, establish baseline usage routines and block abnormal attempts that signal potential threats.
Additionally, Identity Lineage™ delivers key benefits:
- Improved Compliance: Simplify audits with transparent, traceable NHI activity, ensuring adherence to regulatory requirements.
- Operational Efficiency: Eliminate redundancies, streamline troubleshooting, and ensure NHIs are purposeful and secure, boosting productivity across the enterprise.
- Enhanced Scalability: Support the growing number of NHIs as enterprise environments evolve, particularly with the rise of Agentic AI. This new wave of AI-driven automation relies heavily on NHIs to drive efficiency, making scalable management more critical than ever.
This comprehensive approach not only fortifies security but empowers organizations to operate more effectively, even in the face of increasingly complex environments.
Why It Matters Now
The exponential growth of NHIs, combined with increasingly sophisticated cyber threats, has revealed the inadequacy of traditional identity security and management approaches. Modern security isn’t just about locking doors; it’s about understanding why the door exists, who uses it, and where it leads.
Full visibility and context are no longer optional—they are essential. These elements not only strengthen defenses but also enable scalable management of NHIs as their numbers continue to grow. This need is especially urgent in an era where Agentic AI and automation increasingly rely on NHIs to drive efficiency and innovation.
Identity Lineage™ is more than a tool—it’s a philosophy. It delivers the actionable intelligence and clarity required to secure, manage, and optimize the digital ecosystems that modern organizations depend on. At Clutch, as champions of the Zero Trust approach for NHIs, our ethos is simple yet profound: It’s all about trust, and trust begins with knowing and understanding exactly who—or what—you are facing.