When it comes to Zero Trust, the cybersecurity world often focuses on human identities—who’s accessing what, from where, and under what conditions. But there’s another dimension often overlooked in this conversation: non-human identities (commonly abbreviated as NHIs). These are the service accounts, API keys, OAuth tokens, and other machine identities quietly running in the background of modern enterprise IT environments. And while they’re often invisible to users, they’re critical to implementing a true Zero Trust architecture.
Let’s explore why NHIs are fundamental to Zero Trust strategies and how they align with the framework’s principles.
Zero Trust 101: A Quick Recap
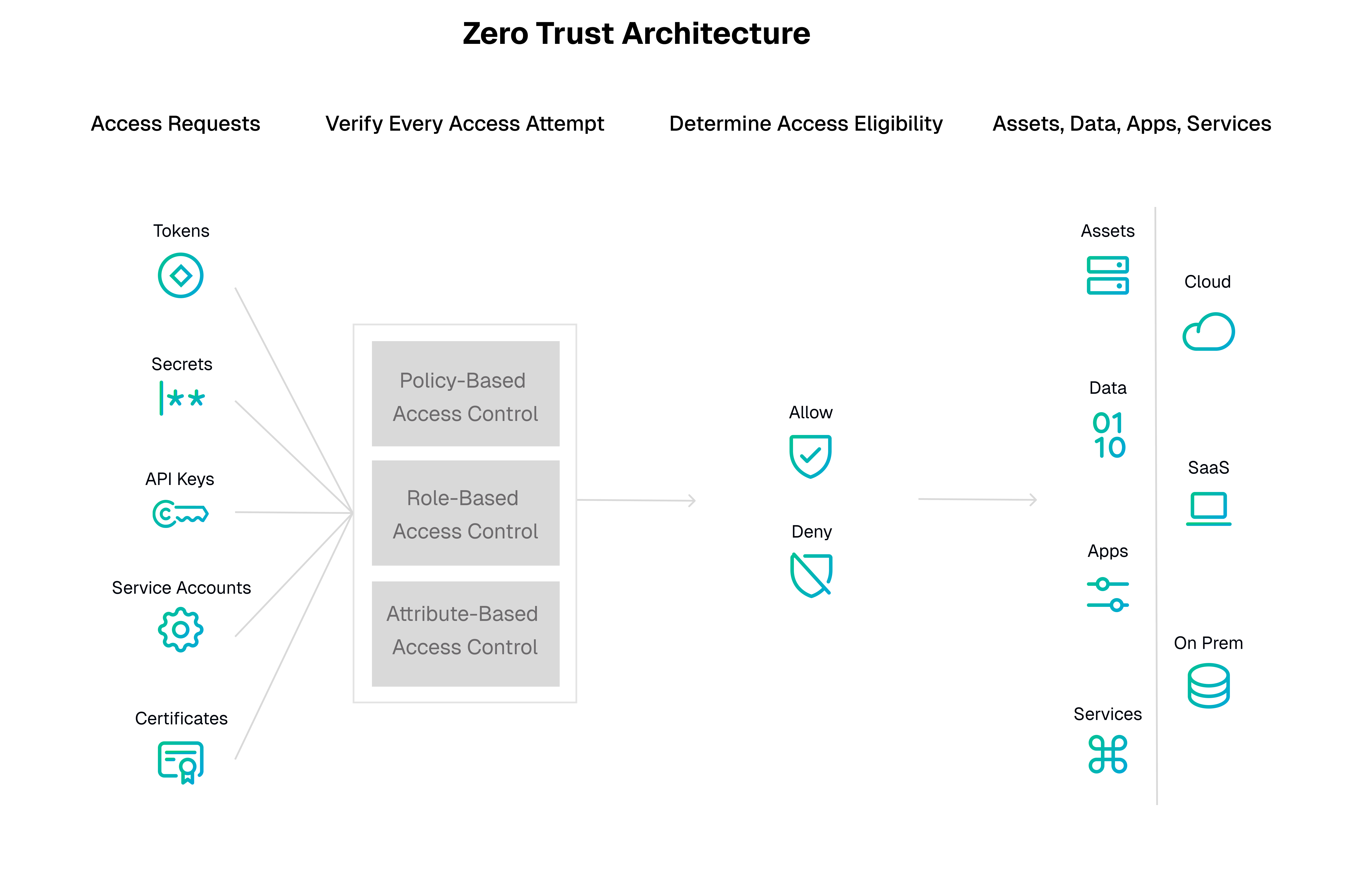
The core philosophy of Zero Trust is simple: “Never trust, always verify.” It assumes that no entity—whether inside or outside the network—should be trusted by default. Access must be continuously validated, and permissions should align strictly with the principle of least privilege.
Zero Trust isn’t a product—it’s a strategy. Its pillars include:
- Identity verification
- Granular access controls
- Continuous monitoring and analytics
- Data protection

Most organizations understand how to apply these principles to human users through technologies like MFA, user behavior analytics, and conditional access policies. But NHIs often fall through the cracks, leaving gaping vulnerabilities in what should be a secure system.
The NHI Problem: A Blind Spot in Zero Trust
Modern applications rely on NHIs to function. APIs communicate across microservices, cloud workloads exchange data, and automation scripts connect systems to deliver seamless user experiences. These non-human entities have privileged access to critical infrastructure, sensitive data, and key operational systems. Yet, they’re often:
- Hardcoded in plaintext within scripts or repositories.
- Overprivileged, granting them broad access beyond their intended purpose.
- Long-lived, persisting for years without revocation or visibility.
- Invisible to monitoring tools, making them ideal targets for attackers.
When attackers breach NHIs, they don’t need to rely on phishing emails or brute force attacks. They simply exploit these exposed keys and tokens to move laterally, escalate privileges, or exfiltrate sensitive data. This fundamentally violates the Zero Trust principle of minimizing attack surfaces.
NHIs and the Zero Trust Framework
To align with the Zero Trust model, organizations must treat NHIs with the same rigor they apply to human identities. Here’s how NHIs intersect with key Zero Trust principles:

Verify Every Identity
Zero Trust mandates robust identity verification for every access request. NHIs, however, are often excluded from this process. APIs and scripts calling sensitive endpoints need the same stringent checks as human logins:
- Strong authentication: Use short-lived, signed tokens (e.g., OAuth 2.0) instead of long-lived static credentials.
- Context-based validation: Ensure NHIs are accessing resources only from known environments, such as specific IP ranges or workloads.
Implement Least Privilege
Many NHIs are overprivileged by default. For example, a single API key might grant read-write access across multiple cloud buckets when it only needs read access to one. Adopting a Zero Trust strategy means:
- Auditing all NHI permissions and revoking unnecessary access.
- Enforcing granular scopes for APIs, ensuring NHIs can perform only their intended functions.
Continuously Monitor and Adapt
Zero Trust is dynamic, requiring constant evaluation of identity behavior. For NHIs, this translates to:
- Behavioral baselining: What does “normal” look like for this NHI? Is it suddenly accessing a region it never accessed before?
- Anomaly detection: Using tools that can flag suspicious activity tied to NHIs, like unusual spikes in API calls or unauthorized resource access.
Segment Resources
NHIs are often granted broad access across environments. Zero Trust encourages segmentation to contain breaches and minimize risk. For NHIs, this means isolating API calls and services to specific environments or network segments.
The Hidden Potential of NHIs in Zero Trust
NHIs aren’t just a risk—they’re also an opportunity. When managed correctly, NHIs can be leveraged to strengthen a Zero Trust strategy. For instance:
- Automation in threat detection: NHIs can provide telemetry data to detect lateral movement within the network.
- Programmatic enforcement: Policies tied to NHIs can dynamically adjust based on contextual signals like time of day or system health.
When NHIs are made visible, secured, and monitored, they become active participants in a Zero Trust ecosystem.
Closing the NHI Gap
Organizations aiming for true Zero Trust must stop treating NHIs as secondary. They need to inventory every machine identity, map its permissions, and integrate it into their Zero Trust framework. Tools and platforms that specialize in managing NHIs—like Clutch Security—make this process scalable, allowing security teams to focus on strategy rather than firefighting.
Zero Trust isn’t just a checkbox or a buzzword; it’s a shift in mindset. By bringing NHIs into the fold, you’re not only closing critical security gaps—you’re fortifying your entire architecture against the evolving threat landscape.
The future of Zero Trust isn’t just human. It’s non-human too.