As our reliance on automation and cloud services grows, so too does the complexity of securing Non-Human Identities (NHIs)). These digital credentials—used by machines, applications, and automated processes to perform operations—have become a fundamental part of today’s enterprise environments. But with this rise comes a major issue: the widespread use of NHIs is largely misunderstood, and their management often lacks the attention and rigor applied to human identities.
At Clutch, we recognized a troubling disconnect. NHIs are everywhere—spanning Cloud, SaaS, legacy on-premise data centers, and everything in between—yet so many organizations don’t fully grasp the risks they’re inheriting by using these services. That’s why we created the NHI Index.
Why We Built the NHI Index
When we started investigating the landscape of NHIs, we were struck by two things: their sheer prevalence and the lack of awareness around managing them securely. The term “NHI debt” comes to mind—a build-up of unmonitored, unmanaged, or over-privileged NHIs that increases your attack surface without you even realizing it. Think about it: every time you adopt a new cloud service, spin up a CI/CD pipeline, or integrate a SaaS app, you're likely adding more NHIs to your environment.
What’s even more concerning is how these NHIs move through different landscapes. They’re not isolated within one environment; they traverse from cloud services to SaaS, from CI/CD pipelines to code repositories, connecting to vaults and even legacy on-prem systems. This interconnectedness can make it incredibly hard to track, let alone secure, every single identity that’s interacting with your most sensitive resources.
We realized the security community needed a resource to bring all of this into focus—a place to catalog these identities, understand their usage, and provide actionable strategies to reduce the risks they pose. The NHI Index is our response to this need.
Understanding the NHI Challenge
What makes NHIs so challenging to manage? They’re fragmented across different platforms—each with its own set of rules and controls. Unlike human identities, which benefit from features like multi-factor authentication (MFA) and centralized oversight, NHIs often operate with far fewer controls. This creates:
- Visibility Gaps: NHIs can go unmonitored, accumulating excessive privileges or becoming stale, making them vulnerable to exploitation.
- No Standardization: Each environment has its own way of handling NHIs, complicating security efforts. Unlike human identities, NHIs don't benefit from uniform control mechanisms.
- Increased Attack Surface: Unmanaged or over-privileged NHIs contribute to an expanded attack surface. High-profile breaches have shown how easy it is for attackers to exploit these hidden vulnerabilities.
One of the most common misconceptions we encounter is the belief that managing NHIs is as simple as rotating keys and tokens. This approach often creates a false sense of security. In reality, even frequent rotations don’t offer real protection—if a secret is compromised, attackers need only minutes to exploit it, long before the next rotation occurs. Moreover, relying on manual or even automated rotations increases friction between security and engineering teams, creating dependencies and unnecessary complexity. The real solution lies in adopting a zero-trust architecture, where access is continuously verified in real-time. This approach eliminates reliance on static secrets and ensures that each interaction is secure, regardless of whether a key has recently been rotated.
What You’ll Find in the NHI Index
- Detailed NHI Catalog:
The NHI Index provides an exhaustive list of NHIs in use across major cloud providers, CI/CD solutions, SaaS platforms, and more. Each entry includes details like service names, environments, and security features, such as audit logs. Many assume NHIs are limited to IAM services, but the Index shows just how many NHIs are inherently tied to the operation of cloud services themselves—NHIs you might not even know exist in your environment.
For example, here’s a glimpse of the NHI landscape within AWS: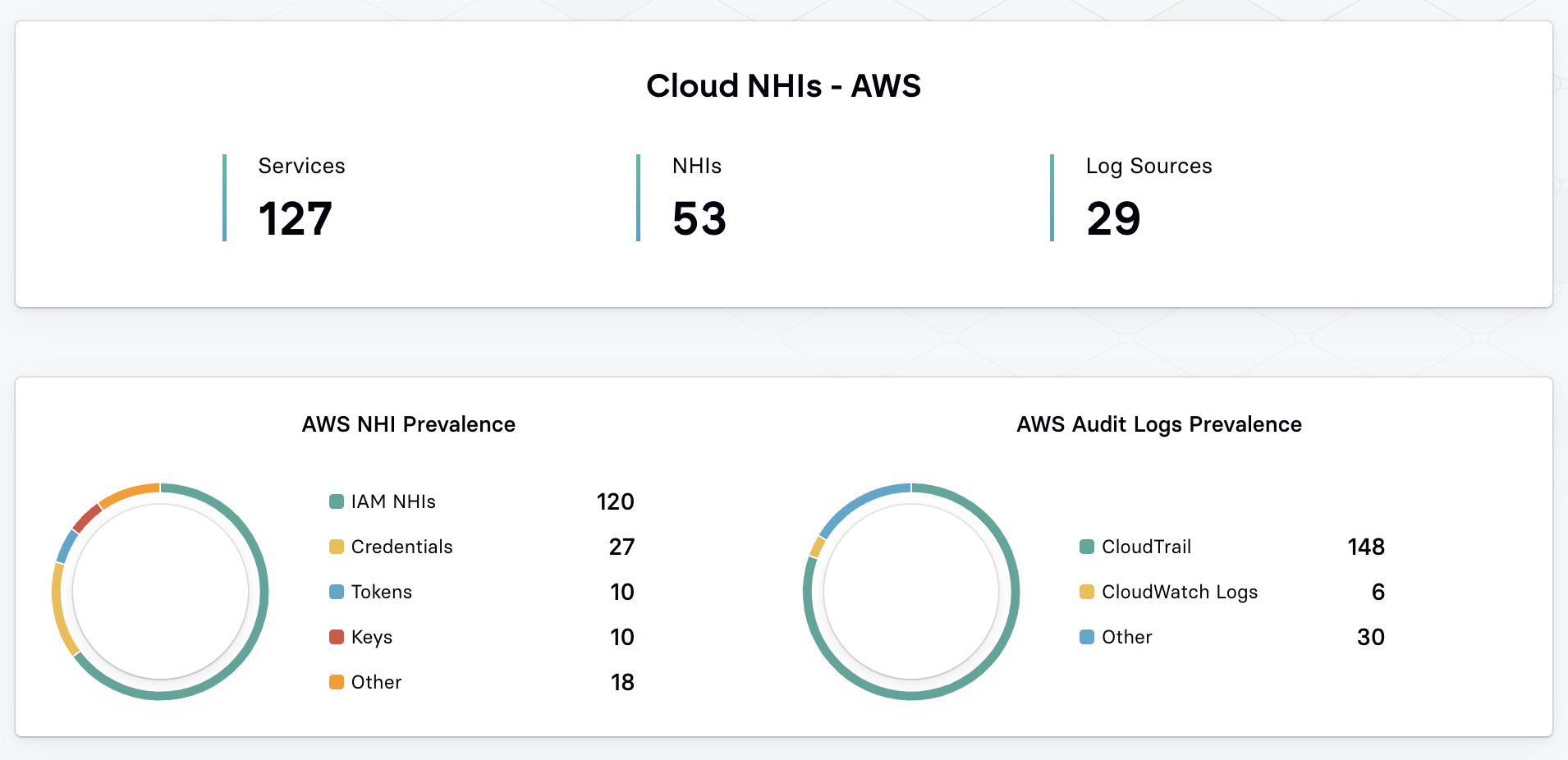
- Essential Resources for Reducing NHI Attack Surfaces:
Securing NHIs requires more than just knowing they exist. The NHI Index offers practical guides on establishing secure connections between cloud service providers (CSPs) and version control systems using OpenID Connect (OIDC) and creating inter-cloud connectivity using ephemeral keys.
We’ve created a tool we named Federator, which includes Terraform scripts and tutorials on Federated Cloud Security and CI/CD-CSP Federation, helping teams minimize the use of static NHIs and reduce their attack surfaces, These Terraform scripts offer a comprehensive example of role federation across all three major cloud providers and CI/CD systems, accompanied by a demonstration video for a complete learning experience.
One of the key resources is a guide on Secretless IAM, which walks users through best practices of using an ephemeral approach in each CSP, based on the native available capabilities. This process drastically reduces the reliance on long-lived credentials, replacing them with ephemeral identities—an essential step in modern NHI security practices.
Why This Matters
The NHI Index is more than just a tool—it’s a call to action. Every enterprise today is using NHIs, whether they know it or not. And with every service, pipeline, or application that touches your infrastructure, more NHIs are introduced. Without a solid strategy for managing them, you're leaving doors open for attackers.
We built this resource to make it easier for security teams to understand, track, and secure their NHIs. By centralizing knowledge and providing actionable steps, the NHI Index demystifies the complexities of NHI security, helping organizations of all sizes to stay ahead of evolving threats.
Explore the NHI Index
We invite you to dive into the NHI Index, explore the catalog, and leverage the resources available to enhance your organization’s security posture. As NHIs become more integral to enterprise operations, securing them isn’t just a best practice—it’s essential. Let’s work together to reduce the risks and protect the future of digital infrastructure.
The NHI Index is available at https://www.nonhuman.id/