TL;DR
Another day, another security breach—this time impacting the popular animation library lottie-player. Just earlier this month, a similar breach at the Internet Archive exposed tokens and highlighted how easily attackers can exploit even a brief exposure. In this lottie-player incident, malicious versions (2.0.5–2.0.7) were uploaded to npm, infecting users with crypto-mining code. This incident makes it clear that the risks of weak token management in supply chains and the importance of Zero Trust in securing NHIs across development environments.
What Is Lottie Player?
lottie-player is an open-source tool that renders animations in web and mobile apps, allowing developers to integrate high-quality, scalable animations with a minimal performance impact. It’s widely used for interactive visual elements, making it an appealing target for attackers aiming to reach a broad user base.
The Incident: Tokens Exposed (Again!)
This breach points to a stolen or leaked npm token, this time from one of the maintainers of lottie-player, known as Aidosmf. Unlike typical releases deployed through the project’s GitHub repository, these malicious versions were published directly from the maintainer’s npm account, indicating a compromise. Once again, we’re seeing how even a brief token exposure can lead to a major security event.
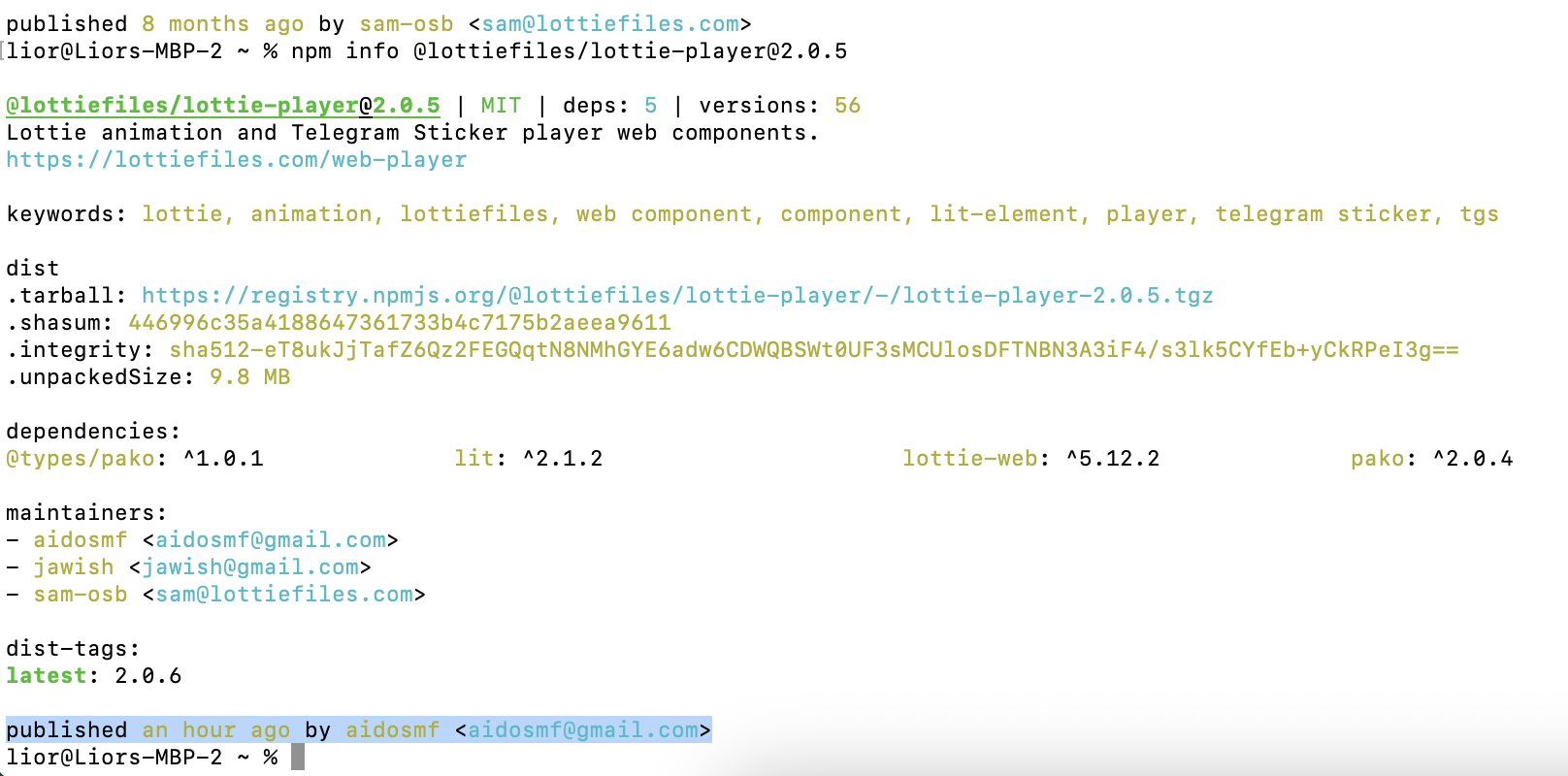
It’s possible that even a momentary accidental exposure of the token triggered this breach. Given the standard npm token patterns and publicly available regex patterns to identify them (e.g., "\\b([0-9Aa-f]{8}-[0-9a-f]{4}-[0-9a-f]{4}-[0-9a-f]{4}-[0-9a-f]{12})\\b" or "(npm_[0-9a-zA-Z]{36})"), it takes mere seconds for an attacker to seize a leaked token and act upon it.
With attackers only managing to push malicious code for around three hours, the damage was limited this time. However, had the breach gone unnoticed, the impact could have been severe, as attackers gain the ability to spread malicious code to unsuspecting users. This serves as a critical reminder: a single compromised token can unlock the door to widespread supply chain attacks, and in npm’s case, standard token patterns and regex identifiers make exposed tokens easy prey.
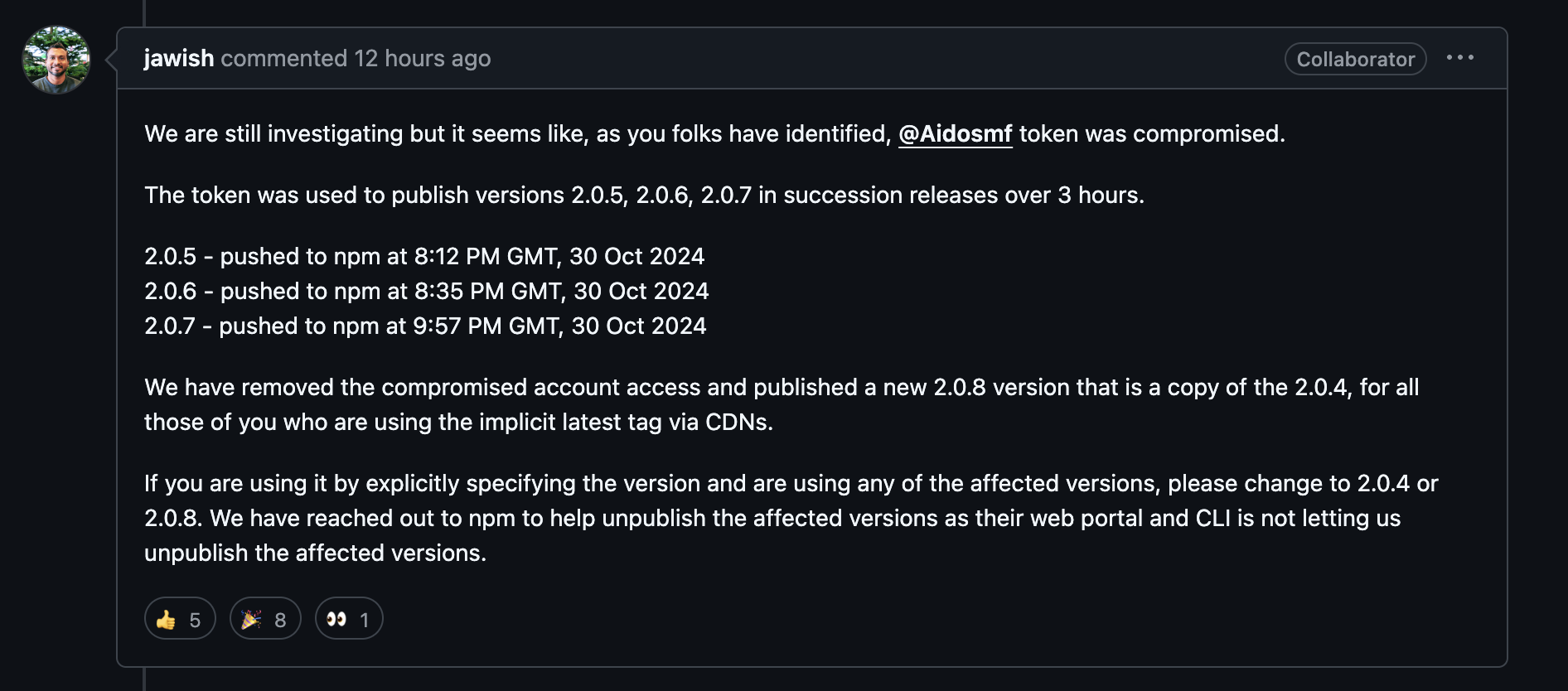
Lessons for Package Maintainers: Securing Tokens with Restriction
This incident highlights a valuable security feature on npm—token restriction to specific IP ranges. How could the maintainers of `lottie-player` have avoided this?
By applying IP-based restrictions, maintainers can limit token access to only authorized devices, making unauthorized usage nearly impossible. This added layer of control is essential for reducing risk in supply chains where token misuse remains a prime attack vector.
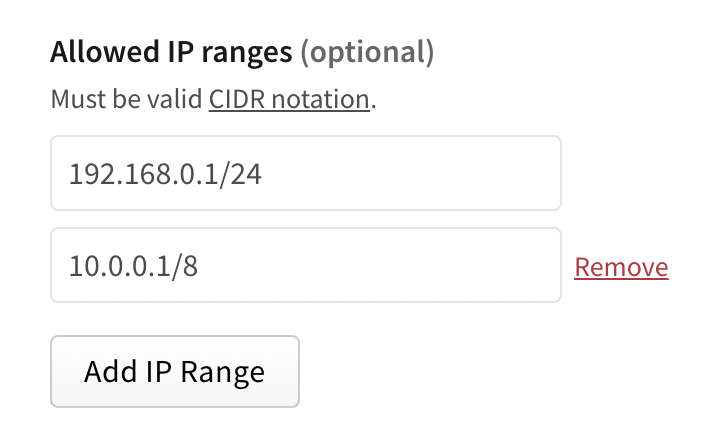
Source: npmjs documentation
Protection Tips for Users
Users also have a role to play. By locking dependencies to specific, verified versions, users of lottie-player who limited their version to pre - 2.0.5 releases remained unaffected by this crypto-miner. Version locking is a critical practice in all development environments, especially when using open-source packages, as it prevents inadvertent upgrades to compromised versions.
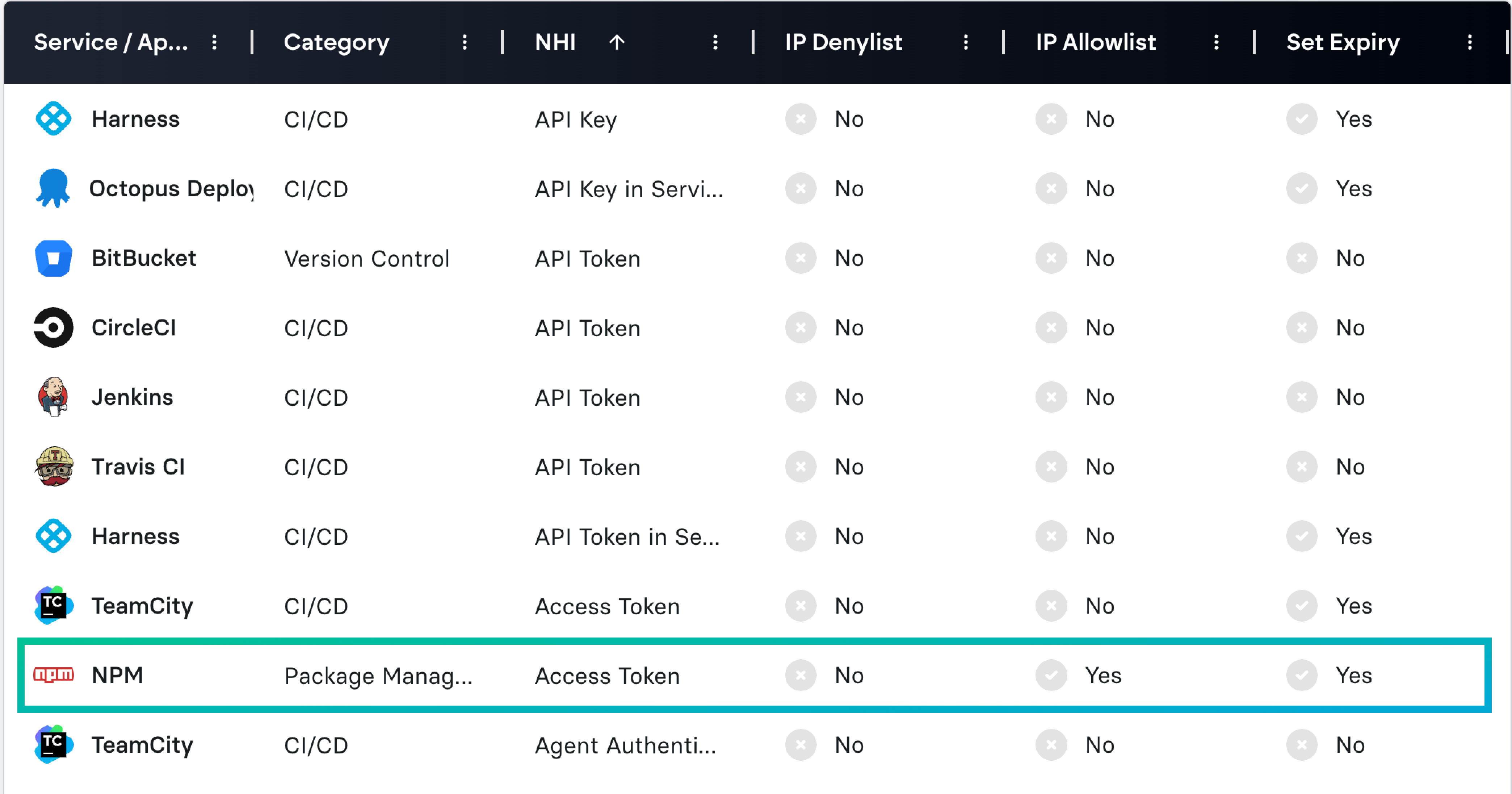
Our NHI Index maps hundreds of NHIs across diverse environments and their security features, covering npm as well (under the Code/CI/CD section), allowing security teams to gain sharper insights into enhancing visibility and monitoring for services utilizing NHIs, just like npm does. Explore more here: https://non-human.id
Final Thoughts: Implementing Zero Trust to Prevent Token Breaches
The recent attack on lottie-player highlights the critical importance of Zero Trust principles for securing tokens and other Non-Human Identities. Zero Trust ensures that every access request is rigorously monitored, verified, and restricted, regardless of the consumer source. By enforcing least privilege, limiting token usage to verified IP addresses or specific devices, and continuously monitoring for abnormal access patterns, organizations can prevent attackers from exploiting exposed tokens.
In today’s landscape of supply chain threats and token leaks, Zero Trust is not just an option; it’s essential for safeguarding sensitive assets and securing popular libraries like lottie-player.





