In a world where digital preservation is paramount, the Internet Archive stands as the guardian of our collective online memory. Yet, even this bastion of historical data isn't immune to modern cybersecurity threats. Recently, it experienced a significant breach that serves as a cautionary tale for organizations worldwide.
Imagine leaving the front door of your house unlocked for two years. That's essentially what happened when a plaintext GitLab token was left exposed in a publicly accessible configuration file from November 2022 until October 2024. Attackers stumbled upon this token—it was like finding a master key. But they didn't stop there; inside the unlocked house, they found another key—a plaintext Zendesk token hidden within the source code repositories.
With access to Zendesk, the attackers delved into sensitive customer support tickets, uncovering personal data and confidential internal communications. This wasn't a smash-and-grab; it was a month-long "rolling breach" that went unnoticed, highlighting critical failures in token management and monitoring.
Let's dive in and understand what we can learn from this incident.
Token Neglect: A Lesson in Complacency
Despite receiving warnings, the Internet Archive didn't revoke these exposed tokens promptly. They remained active longer than they should have, which goes against fundamental security protocols. The tokens provided broad, unrestricted access, amplifying the potential damage when they fell into the wrong hands. Additionally, there were insufficient policies governing who could create, access, or distribute these tokens. This lack of oversight turned what should have been a manageable risk into a prolonged security issue with significant impact.
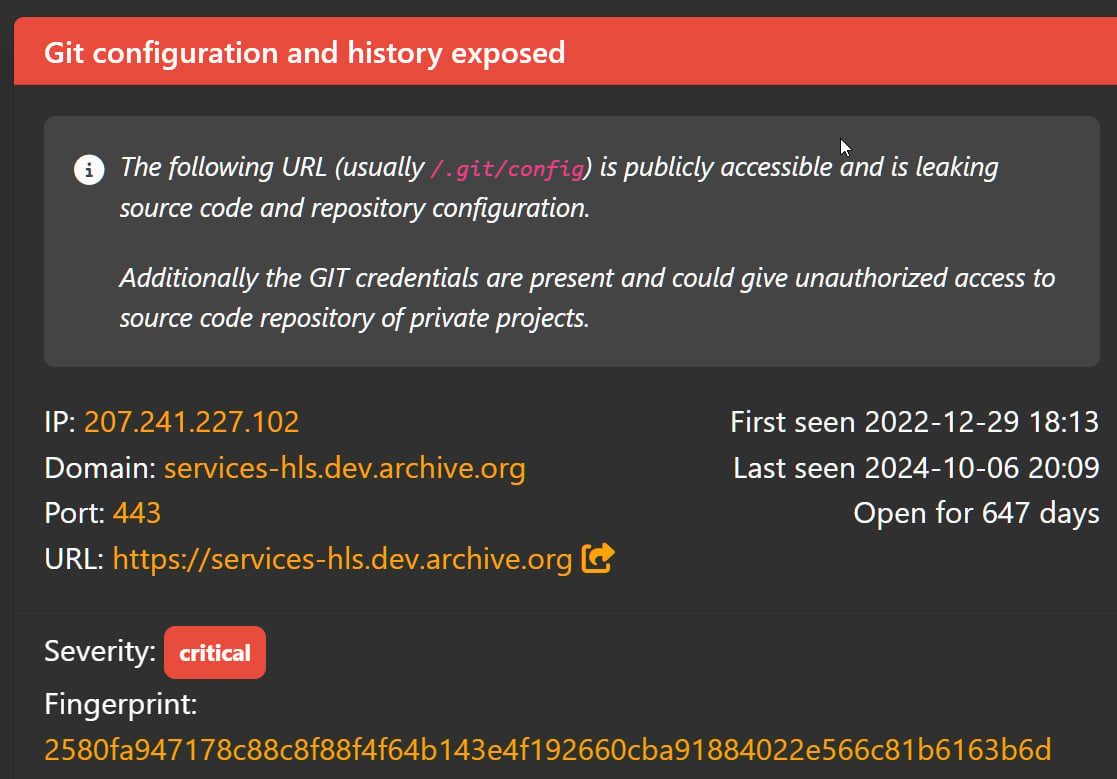
Source: BleepingComputer
These oversights effectively left the door open for attackers. Failing to implement essential token management practices allowed the breach to continue unchecked, highlighting how crucial it is to treat tokens with the same level of security as passwords or other sensitive credentials.
GitLab's Logging Blind Spot
One of the most troubling aspects of this breach is what we don't know—and that's due to GitLab's insufficient logging capabilities. GitLab doesn't log read operations for tokens, creating a significant blind spot. Without records of what was accessed, it's nearly impossible to determine the full extent of the data that attackers may have viewed or stolen.
This lack of visibility hampers any forensic investigation. How do you assess the damage when you can't see what's been taken? It also raises compliance concerns. Regulations like GDPR and HIPAA require organizations to protect personal data and report breaches accurately. Without detailed logs, meeting these obligations becomes a daunting task.
GitLab does however offer extensive analysis capabilities for write-type operations and actions taken by authenticated entities.
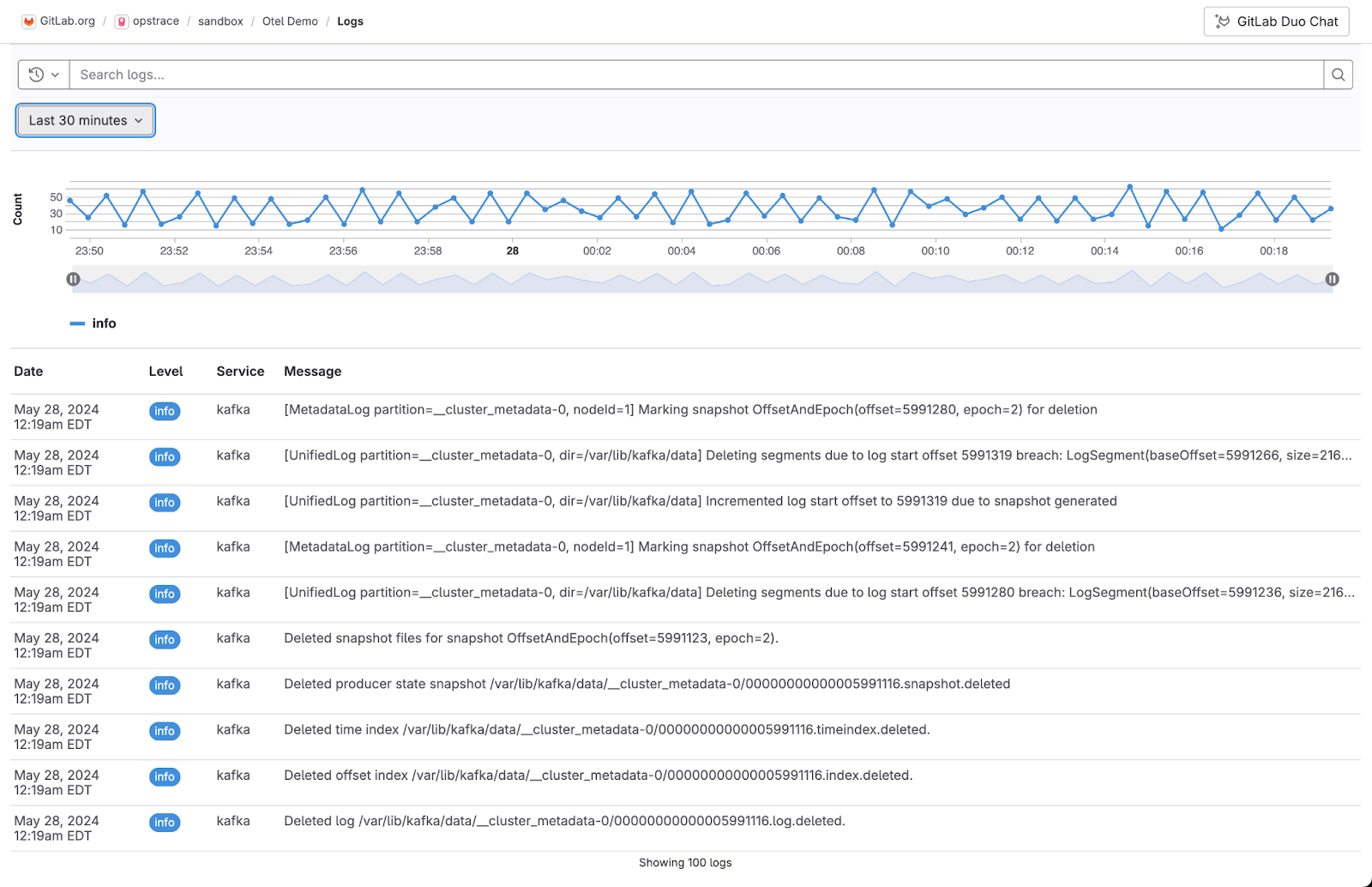
This is yet another wake-up call for security leaders. You can't protect what you can't monitor. The absence of comprehensive logging means that, even with other security measures in place, you may still be blind to significant vulnerabilities and breaches.
Zendesk's Audit Logs: A Beacon In The Dark
In contrast to GitLab, Zendesk offers detailed audit logs accessible through its API. These logs can be a lifesaver, allowing organizations to monitor API token usage closely. By filtering events with source_type set to apitoken, teams can track which tokens are active, how they're used, and spot any unusual activity.
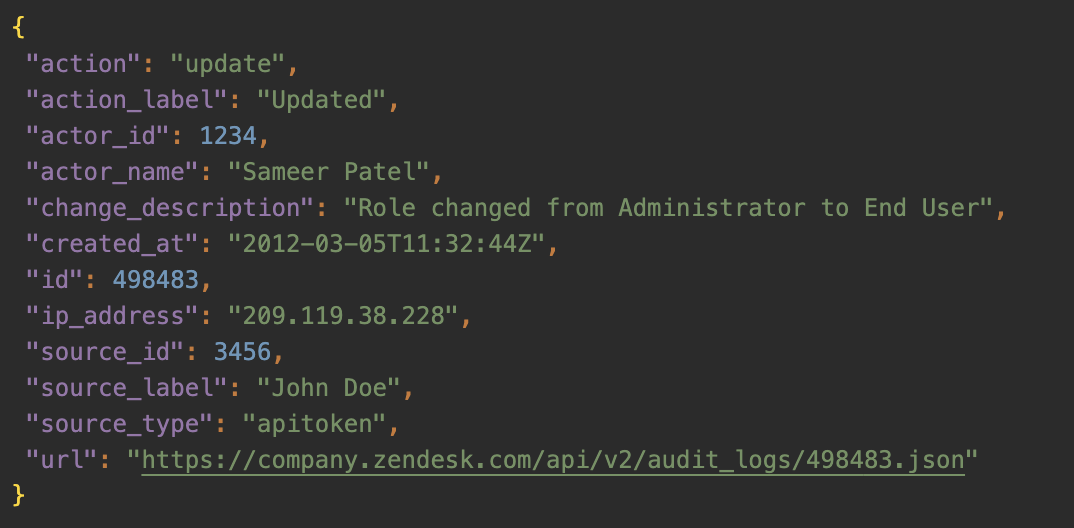
Timestamps and originating IP addresses provide additional layers of insight, helping to identify suspicious activities in real-time. This kind of visibility is crucial for quick response and remediation. However, these logs are only valuable if organizations actively monitor and analyze them. It's not enough for the tools to exist; they must be leveraged effectively to enhance security posture.
Clutch Security's NHI Index: Taking Back Control
Managing Non-Human Identities like tokens and API keys has become increasingly complex. Clutch Security offers a solution with its NHI Index, an industry mapping tool that helps security teams gain visibility into all NHIs across the enterprise. Understanding where these identities exist, their context, and how they're used is the first step in securing them.
The NHI Index enables organizations to enforce governance by applying policies that control access and permissions effectively. By integrating seamlessly with platforms like GitLab and Zendesk, Clutch Security fills the gaps left by insufficient native logging and monitoring tools. If misuse or anomalies are detected, automated workflows can immediately notify teams or revoke compromised tokens, minimizing risks and potential damage.
Moving Forward: Proactive Steps for Security Leaders
This breach underscores the importance of taking proactive measures. Security leaders and technical stakeholders should view this incident as a catalyst to review and strengthen their own practices. Start by conducting a comprehensive token audit to identify all active tokens, their permissions, and where they're stored.
Implement strict token policies that enforce regular rotation, apply the principle of least privilege, and mandate immediate revocation when necessary. Enhance your monitoring solutions by deploying tools that offer comprehensive logging—including read operations—to ensure you have full visibility into your systems.
Education is also key. Training employees on the importance of secure token handling and the risks associated with exposure can prevent accidental vulnerabilities. Remember, security isn't just about tools and protocols; it's about people and practices working together.
Lessons Learned
The Internet Archive breach is a stark reminder of how easily overlooked elements can become significant security liabilities. Visibility is crucial—you can't defend against threats you can't see. Tokens and API keys are high-value targets for attackers and should be guarded with the same rigor as any other sensitive credential.
Proactive measures save time and resources. Early detection and swift response can prevent a minor oversight from escalating into a full-scale crisis. By taking control of token management and enhancing monitoring capabilities, organizations can significantly reduce their risk profile.
Conclusion: Don't Let Tokens Be Your Achilles' Heel
In today's digital landscape, attackers are constantly seeking the path of least resistance. Don't let unsecured tokens and API keys be that path. The Internet Archive's experience serves as a powerful lesson in the importance of diligent token management and robust monitoring.
For technical stakeholders and security leaders, the message is clear: Act now to secure your Non-Human Identities before they become the weakest link in your security chain. By implementing comprehensive strategies and leveraging advanced tools, you can protect your organization's assets and maintain the trust of your users and partners.





